The following is a writeup on the process used to get the invite code for HackTheBox
HackTheBox is a great website which contains pentesting labs to develop your security skillset. To create an account and gain access to the labs you first need to get an invite code and enter it into the URL https://www.hackthebox.eu/invite
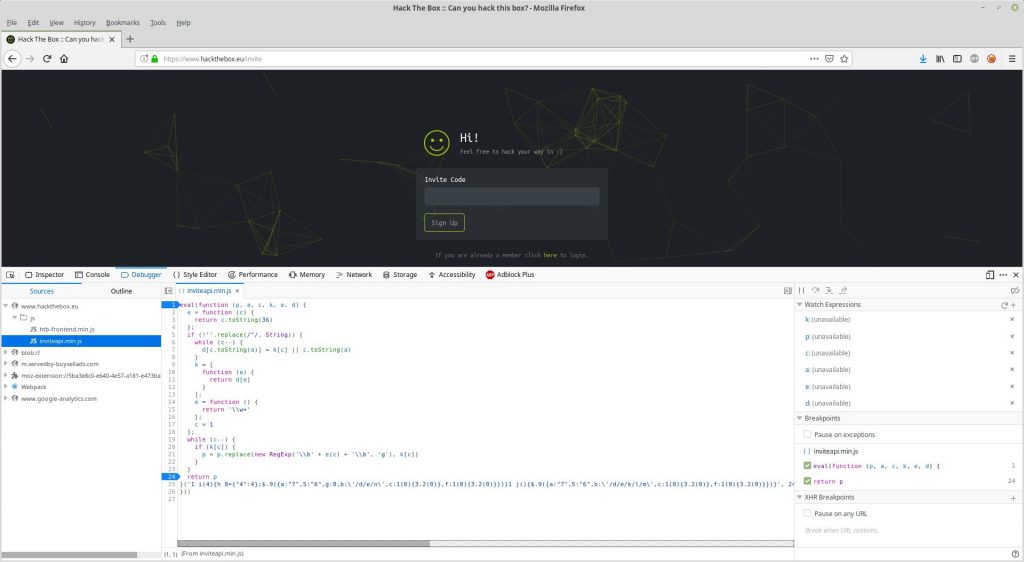
The first stage when greeted with a page like this is to view the source and have a look to see whats happening in the background. For my testing I used firefox so by right clicking on the page and clicking “Inspect Element” it bring up the source code for the page. By clicking on the debugger tab I noticed there was a js directory containing the file inviteapi.min.js located at https://www.hackthebox.eu/js/inviteapi.min.js. I then opened the file through the firefox debugger tab.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
eval(function (p, a, c, k, e, d) {
e = function (c) {
return c.toString(36)
};
if (!''.replace(/^/, String)) {
while (c--) {
d[c.toString(a)] = k[c] || c.toString(a)
}
k = [
function (e) {
return d[e]
}
];
e = function () {
return '\\w+'
};
c = 1
};
while (c--) {
if (k[c]) {
p = p.replace(new RegExp('\\b' + e(c) + '\\b', 'g'), k[c])
}
}
return p
}('1 i(4){h 8={"4":4};$.9({a:"7",5:"6",g:8,b:\'/d/e/n\',c:1(0){3.2(0)},f:1(0){3.2(0)}})}1 j(){$.9({a:"7",5:"6",b:\'/d/e/k/l/m\',c:1(0){3.2(0)},f:1(0){3.2(0)}})}', 24, 24, 'response|function|log|console|code|dataType|json|POST|formData|ajax|type|url|success|api|invite|error|data|var|verifyInviteCode|makeInviteCode|how|to|generate|verify'.split('|'), 0, {
}))
As you can see on the second from last line, there is a function listed called makeInviteCode which based on the name is exactly what we need to execute.
So to run makeInviteCode I switched to the console tab in the developer tools where you are greeted with the following output:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
. .
. uuuuuuu .
. uu$$$$$$$$$$$uu .
. uu$$$$$$$$$$$$$$$$$uu .
. u$$$$$$$$$$$$$$$$$$$$$u .
. u$$$$$$$$$$$$$$$$$$$$$$$u .
. u$$$$$$$$$$$$$$$$$$$$$$$$$u K E E P C A L M .
. u$$$$$$$$$$$$$$$$$$$$$$$$$u .
. u$$$$$$" "$$$" "$$$$$$u A N D .
. "$$$$" u$u $$$$" .
. $$$u u$u u$$$ H A C K .
. $$$u u$$$u u$$$ .
. "$$$$uu$$$ $$$uu$$$$" T H I S .
. "$$$$$$$" "$$$$$$$" .
. u$$$$$$$u$$$$$$$u B O X .
. u$"$"$"$"$"$"$u .
. uuu $$u$ $ $ $ $u$$ uuu .
. u$$$$ $$$$$u$u$u$$$ u$$$$ .
. $$$$$uu "$$$$$$$$$" uu$$$$$$ .
. u$$$$$$$$$$$uu """"" uuuu$$$$$$$$$$ .
. $$$$"""$$$$$$$$$$uuu uu$$$$$$$$$"""$$$" .
. """ ""$$$$$$$$$$$uu ""$""" .
. uuuu ""$$$$$$$$$$uuu .
. u$$$uuu$$$$$$$$$uu ""$$$$$$$$$$$uuu$$$ .
. $$$$$$$$$$"""" ""$$$$$$$$$$$" HackTheBox v0.9.3 .
. "$$$$$" ""$$$$"" info@hackthebox.eu .
. $$$" $$$$" .
. .
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
From here, I entered into the input box at the bottom makeInviteCode() and pressed enter. This generated the following output:
1
2
3
4
5
makeInviteCode()
undefined
0: 200
data: Object { data: "SW4gb3JkZXIgdG8gZ2VuZXJhdGUgdGhlIGludml0ZSBjb2RlLCBtYWtlIGEgUE9TVCByZXF1ZXN0IHRvIC9hcGkvaW52aXRlL2dlbmVyYXRl", enctype: "BASE64" }
success: 1
As you can see. It has provided us with a string of data encoded in base64. So I opened a terminal windows and entered the following command to decode the base64:
1
2
james@LenovoLaptop:~$ echo SW4gb3JkZXIgdG8gZ2VuZXJhdGUgdGhlIGludml0ZSBjb2RlLCBtYWtlIGEgUE9TVCByZXF1ZXN0IHRvIC9hcGkvaW52aXRlL2dlbmVyYXRl | base64 --decode
In order to generate the invite code, make a POST request to /api/invite/generate
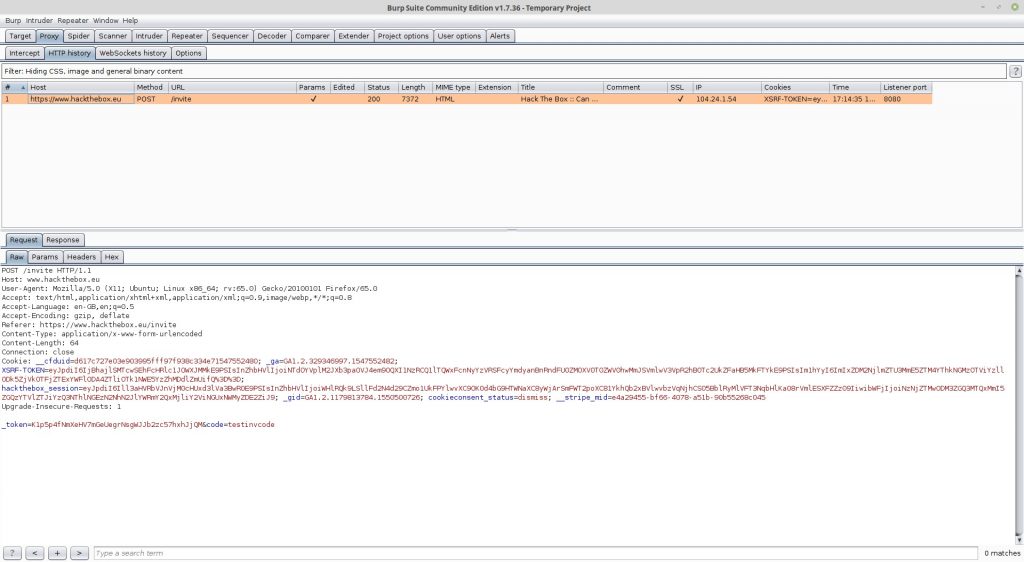
So now we need to send a POST to /api/invite/generate. To do this I used the BURP suite. I browsed to https://www.hackthebox.eu/invite and started the BURP proxy. I then entered random data into the input box and pressed signup. My goal here was to capture a genuine POST request that I could modify to have it send to /api/invite/generate. Once I pressed the signup button BURP successfully captured the POST request I then right clicked the POST request which was captured and selected “Send to Repeater”. This allows you to resend the request and modify it before sending. The following is the default request to be sent:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
POST /invite HTTP/1.1
Host: www.hackthebox.eu
User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:65.0) Gecko/20100101 Firefox/65.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-GB,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: https://www.hackthebox.eu/invite
Content-Type: application/x-www-form-urlencoded
Content-Length: 64
Connection: close
Cookie: __cfduid=d617c727e03e903995fff97f938c334e71547552480; _ga=GA1.2.329346997.1547552482; XSRF-TOKEN=eyJpdiI6IjBhajlSMTcwSEhFcHRlc1JOWXJMMkE9PSIsInZhbHVlIjoiNTdOYVplM2JXb3paOVJ4em9OQXI1NzRCQ1lTQWxFcnNyYzVRSFcyYmdyanBnRndFU0ZMOXV0T0ZWV0hwMmJSVmlwV3VpR2hBOTc2UkZFaHB5MkFTYkE9PSIsIm1hYyI6ImIxZDM2NjlmZTU3MmE5ZTM4YThkNGMzOTViYzllODk5ZjVkOTFjZTExYWFlODA4ZTliOTk1NWE5YzZhMDdlZmUifQ%3D%3D; hackthebox_session=eyJpdiI6Ill3aHVRbVJnVjM0cHUxd3lVa3BwR0E9PSIsInZhbHVlIjoiWHlRQk9LSllFd2N4d29CZmo1UkFPYlwvXC9OK0d4bG9HTWNaXC8yWjArSmFWT2poXC81YkhQb2xBVlwvbzVqNjhCS05BblRyMlVFT3NqbHlKa08rVmlESXFZZz09IiwibWFjIjoiNzNjZTMwODM3ZGQ3MTQxMmI5ZGQzYTVlZTJiYzQ3NThlNGEzN2NhN2JlYWRmY2QxMjliY2ViNGUxNWMyZDE2ZiJ9; _gid=GA1.2.1179813784.1550500726; cookieconsent_status=dismiss; __stripe_mid=e4a29455-bf66-4078-a51b-90b55268c045
Upgrade-Insecure-Requests: 1
_token=K1p5p4fNmXeHV7mGeUegrNsgWJJb2zc57hxhJjQM&code=testinvcode
As you can see from the first line. This POST request is sent to /invite. I changed this to /api/invite/generate and clicked go. I received the following response:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
HTTP/1.1 200 OK
Date: Mon, 18 Feb 2019 17:49:33 GMT
Content-Type: application/json
Connection: close
Vary: Accept-Encoding
Cache-Control: no-cache, private
X-Frame-Options: SAMEORIGIN
X-XSS-Protection: 1; mode=block
X-Content-Type-Options: nosniff
Strict-Transport-Security: max-age=0; includeSubDomains
Expect-CT: max-age=604800, report-uri="https://report-uri.cloudflare.com/cdn-cgi/beacon/expect-ct"
Server: cloudflare
CF-RAY: 4ab254bc9b8ebc5c-LHR
Content-Length: 99
{"success":1,"data":{"code":"VFNPWk4tRUZIR1EtVURMTUctRU9MU1QtV0VGWE8=","format":"encoded"},"0":200}
As you can see the response returned a base64 encoded string. By decoding this string using the same method mentioned previously. It will provide you with the invite code needed to proceed onto the next stage.