At this stage I know very little about the Malware analysis process. I recently purchased a book on the subject called “Practical Malware Analysis” by Michael Sikorski and Andrew Honig. My aim is to read through the book and practice the techniques taught on real examples of malicious code. Updating this blog as i progress.
The first step, which I will detail today is the setup of my virtual lab. For the hardware I have used my old gaming computer. Its not very good at running games anymore but perfect for the malware analysis. I have it installed with Debian Linux distribution and have also installed VirtualBox.
There are pros and cons for using virtualisation for malware analysis. The pros include the ability to create snapshots of the working environment and having the ability to create virtual networks. Which i will explain later. One downside i have read about is some malware will behave differently if it discovers its being run in a virtualised environment. With the sole purpose of preventing it being analysed.
So in my setup i am using VirtualBox to create the virtual machines. I am using a Windows XP Professional machine. Loaded with any tools which i may need. Along with a Debian machine used as a DNS / Mail / IRC server. Some malware will attempt to communicate in some way with something on the internet. Weather it be through IRC, a simple DNS request or through mail protocol. Having a virtual Debian machine with these services installed it allows me to receive the requests and see in more detail what they are doing.
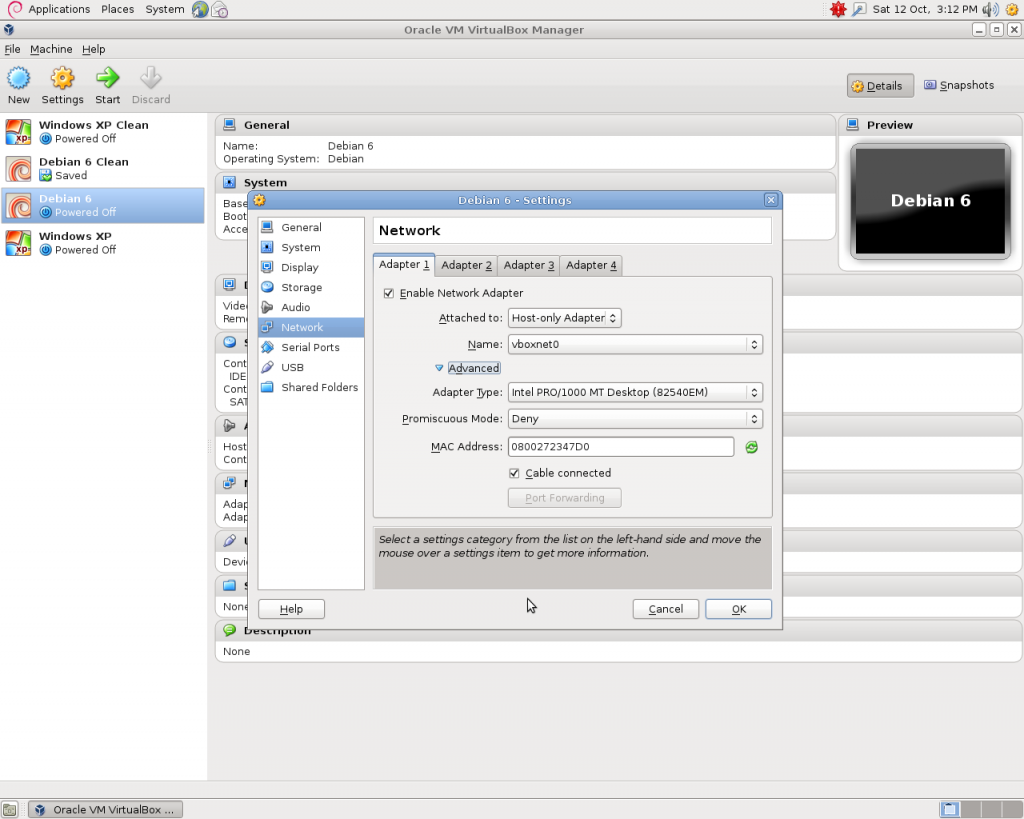
As you can see from the screenshot below, I have created clones of both the virtual machines. This allows me to easily start afresh without having to reinstall all the tools again. Both the machines are in Host only mode and connected to a virtual network called vboxnet0. This prevents the malware escaping from the virtual machine and propagating throughout my network. I am also extremely paranoid and will unplug my network cable from the computer when performing the analysis.
 The only software i will install on Debian to start with is a DNS server. This will allow me to redirect any DNS queries the malware may make to a computer of my choice (Mine). I decided to use Dnsmasq for this purpose as its very simple to setup.
The only software i will install on Debian to start with is a DNS server. This will allow me to redirect any DNS queries the malware may make to a computer of my choice (Mine). I decided to use Dnsmasq for this purpose as its very simple to setup.
I simply installed Dnsmasq with the command:
1
apt-get install dnamasq
And edited the /etc/dnsmasq.conf file to to only allow queries on a specific interface. In my case eth0
1
2
3
4
5
# If you want dnsmasq to listen for DHCP and DNS requests only on
# specified interfaces (and the loopback) give the name of the
# interface (eg eth0) here.
# Repeat the line for more than one interface.
interface=eth0
and to allow for logging of dns requests:
1
2
3
# For debugging purposes, log each DNS query as it passes through
# dnsmasq.
log-queries
I also added into the /etc/hosts file a test record pointing the domain james.com to IP address 66.66.66.66.
1
2
3
4
5
6
7
8
9
10
11
127.0.0.1 localhost
127.0.1.1 debian.localdomain debian
66.66.66.66 james.com james.com
# The following lines are desirable for IPv6 capable hosts
::1 ip6-localhost ip6-loopback
fe00::0 ip6-localnet
ff00::0 ip6-mcastprefix
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
Next i’m going to setup Windows XP to use my virtual Debian machine as a DNS server. I’m not going to explain how i did this. If your reading this you probably know already. I tested the configuration with nslookup.
1
2
3
4
5
6
7
8
9
10
11
12
Microsoft Windows XP [Uersion 5.1.2600]
(C) Copyright 1985-2001 Microsoft Corp.
C:\\Documents and Settings\james>nslookup james.com
*** Can't find server name for address 192.168.56.101: Query refused
*** Default servers are not available
Server: Unknown
Address: 192.168.56.101
Name: james.com
Address: 66.66.66.66
C:\Documents and Settings\james>
As you can see the DNS server responded with the test ip of 66.66.66.66.
I can monitor the DNS requests being made to the server by using the command:
1
tail -f /var/log/syslog
This should turn out useful when running the malware.
1
2
3
james@debian:~$ sudo tail -f /var/log/syslog
Oct 12 15:15:37 debian dnsmasq[1051]: query[PTR] 101.56.168.192.1n-addr.arpa from 192.168.56.102
Oct 12 15:15:37 debian dnsmasq[1051]: query[A] james.com from 192.168.56.102
Now I’m going to detail some of the software I have installed on the target machine. At this stage I haven’t even attempted to look at any malware so I am likely missing some necessary tools. Once the malware is on the machine it won’t have access to the internet. Because of this I have tried to plan ahead and install everything I suspect I will need. There’s a high chance I will miss something having never done this before.
Regshot
This tool allows you to take a snapshot of your machine in two different states and then compare them. For example, you may make a snapshot before and after you have run some malware. Comparing the two snapshots will allow you to see the changes the malware has made to the system. It records new files / folders and registry changes.
Process ExplorerThis is basically task manager in steroids. It allows you to see the processes that are running
WiresharkThis allows you to monitor network traffic In this case in particular, traffic created by the malware.
Process MonitorAllows you to see events which happen when a program is run. For example changes, modifications and execution of files.
CaptureBATAllows you to monitor files and network activity
OllyDebugI have never used this software before. From general reading, it allows you to run a program through it and watch how it interacts with the underlying system. It allows you to see the instructions it executes in the form of assembly language and also the data it stores.
Notepad++A more powerful version of Windows notepad.
StringsPart of the SysInternals suite. It allows you to scan a file for strings (sequence of readable characters)
Once I installed the software above I saved the virtual machine and cloned it. This lets me work on the cloned version when analysing the malware and reverting back to the original clean machine if I need to start again.